|
SOFTWARE-BASED
STUDENT REGISTRATION PROCEDURE USING HTML AND JAVA HOSTED ON THE UNIVERSITY
INTRANET
By
SESAN,
OLUWAGBENGA O. (954318)
AND
SOWANDE,
OLUBUNMI AYOTUNDE (954112)
SUBMITTED TO THE
DEPARTMENT OF ELECTRONIC AND ELECTRICAL ENGINEERING, FACULTY OF ENGINEERING,
IN PARTIAL FULFILMENT
FOR THE AWARD OF B.Sc (Hons) IN ELECTRONIC AND ELECTRICAL ENGINEERING
APRIL
2001
Back to Top
PREFACE
The boundaries
that mark the distinctive location of nations are fast fading off as
technological innovations turn the whole world into a global village.
Education, business, governance, agriculture, automobiles, communications and
all other spheres of human endeavour are not left out in this dynamic
revolution.
Education, particularly, has a lot to do in other
to keep up with the global pace for a balanced society. This poses an automatic
challenge to Universities (in developing nations) as they must endeavour to
restructure their entire systems, protocols and procedures so as to have a good
chance of competing on a global scale.
The course curricula, the registration procedure
and the entirety of processes must be refined to conform with global standards
that would make possible a networked system and prevent isolated operations.
This final year project is borne out of the
desire to see this same change effected in the student registration procedure
at the Obafemi Awolowo University, Ile-Ife, Nigeria. This project, Software Based Student Registration
Procedure using HTML and Java and hosted
on the University Intranet (eRegistration), required
consultations for a proper understanding of the student registration procedure
at the Obafemi Awolowo University, a study of the University’s Intranet and an
application of the knowledge of HTML and Java in converting the tedious manual
procedure into a software-based system.
We believe that this University can pioneer this
phenomenon and thus open up development opportunities for other Nigerian and
African Universities, and the nations they represent.
‘Gbenga Sesan Bunmi Sowande
gbengasesan@yahoo.com
boso@soccermail.com
Back to Top
DEDICATION
Tosin
Sesan, I think I came exactly seven years ahead of you to make some mistakes
you won’t have to make. I believe in you and know that your generation is
waiting for you. I love you!
‘Gbenga Sesan
This
work is dedicated to Babatunde Lawore. I wake up everyday and have to remind
myself that you are no longer with us. Hope to see you on the other side.
Bunmi Sowande
TABLE
OF CONTENTS
Back to Top
1.3
The current registration procedure
Back to Top
2.1
HTML (Hyper Text Markup Language)
2.2
Object-Oriented Programming: Java
2.2.2 Using Non-Object-Oriented Languages
2.2.4 Object Oriented Languages
2.3
Java – the programming language
2.3.2 Java compared with other languages
2.4
The Hardware Aspect – The OAU computer network
2.4.3.1 Proactive Network Management
Back to Top
CHAPTER 3: Software Development
3.1.1 Problem 1: New Client/Server Application Deployment
3.1.2 Problem 2: Migrating to new technologies
3.1.3 Problem 3: Poor Network Performance
3.1.4 Problem 4 – Not Enough Staff
3.1.5 Problem 5 – Network Downtime
Back to Top
4.6
Maintenance, Extension and Redesign
Back to Top
CHAPTER 5: Conclusion and
Recommendation
Back to Top
Appendix B – Sample Screen Shots
Back to Top
.
CHAPTER 1: Introduction
1.1 Background
The
registration procedure in Obafemi Awolowo University, Ile-Ife is a tedious and
often frustrating procedure. Endless queues, and filling out several forms in
quadruplicate may have been adequate ten years ago, but today, the number of students
has astronomically increased and the staff strength is still the same as
before. This leads to long queues and a lot of precious time is wasted while
trying to get your accommodation, pay your tuition and register for your
courses at your department. The process is even more tedious on freshers (new
students) as they have to verify their admission, register at the health centre
and get their accommodation.
A careful study of the process reveals that a lot
of key information is being duplicated and distributed to different places. If
this information could be placed in a central place for everyone to share, a
lot of time and effort will be saved on the part of the student and the
university staff. Also the information will easier to access and store,
removing a large amount of administrative overhead.
By using a central database stored the already
existing university intranet, data could be entered by the students at any
computer on the network, and all the relevant parties that need the information
can retrieve it from there. Although a few things will still need the physical
presence of the student, e.g. medical tests and verification of WAEC results,
using this data will drastically cut down the time spent with each student and
eliminate several unnecessary hassles from the entire process. Using the latest
technology, life will be made easier on both students and staff at the
beginning of each semester.
1.2 Benefits of
the Project
Of the numerous
benefits to the university of the project, the following are worthy of note:
·
Elimination of the
rigours of processing paperwork
·
Reduction of cost
on office expenses, since less of paperwork is done
·
Assurance of
accuracy and speed
·
Upgrade of
University status and relevance in the 21st century
·
Reduction of time
wasted in processing
·
Reduction of cost
on manpower
·
Generation of a student
database that makes for easier retrieval of almost any information on
any registered student at the click of the mouse
·
Automated course
assessment processes.
Most importantly, this project will prepare the
school for full computerisation in the nearest future. As students begin to
register on the network, the student database will over time, contain details
of all students enrolled on campus, meaning that all their grades and
accommodation details are stored on the database and more importantly, can be
retrieved at the click of a mouse. This will make certain processes such as,
issuing of transcripts and compilation of the best students in a particular
class for a recruitment exercise, a lot easier and less time consuming. Also,
instead of going to several different departments to register different
courses, all one has to do is to register all the courses at a central place
and the departments in question will be notified immediately.
Also, the students will benefit from this by
having an easier registration procedure that is more defined and structured.
This will reduce the tension at the beginning of every semester for both staff
and students, and allow them to have a relaxing start to the semester.
1.3 The current
registration procedure
We studied the registration procedure for new students,
popularly known as Jambites or Freshers. They need to register at three
basic places:
1.
Their faculties,
which pass the information to the Directorate of Student Affairs
2.
The health centre
3.
Their departments,
where they submit the list of courses they registered.
Also, the students have to go to the various
departments offering the courses they wish to register, and register the courses.
With the current method of registration, this
process can take up to a month. Also, the students are subjected to long queues
and coming back indefinitely to the same place while waiting for the staff to
be ready for them.
The entire process is outlined below:
1.
The student goes to
the faculty for screening. This involves the verification of the students UME
score (University Matriculation Examination) and SSCE (Senior Secondary
Certificate Examination) to ascertain that the student is suitable for admission.
2.
The student goes to
the bursary to pay the prescribed fees. This can only be done after clearance
has been given from the faculty office.
3.
The student goes to
the health centre for medical tests and registration. The following tests are
administered
i.
Blood test
ii.
Urine test
iii.
Chest X-Ray
4.
Allocation of a
room at the halls of residence. This is ‘guaranteed’ for all new and final year
students, but returning students have to apply and wait to see if they will be
given a room.
5.
Submission of
course forms at the department the student has been admitted into. By the time
the student does this, he would have been to the various departments offering
the courses he wishes to take and ‘signed’ the courses. (Registered for them)
This current method has the following disadvantages:
i.
The process is
extremely slow.
ii.
The registration
takes place at several different venues, making it an extremely tiring
procedure.
iii.
The entire process
is laden with excessive protocol and unnecessary issues as well as submitting
the same information at several different places.
iv.
The students have
to visit the health centre in a haphazard manner, and the medical examination
is extremely chaotic and strenuous.
We can now see how outdated the current procedure
is. Also by studying the various forms used, we can see that the bulk of
information on them is duplicated again and again.
This is
the list of the forms used :
1.
MIS01 – Student’s Information Form (4 copies)
This form contains basic
information about the student.
2.
MIS02 – Course Registration Form (4 copies)
This form contains information
on the academic plans of the student for a semester, basically listing all the
courses the student is planning to take.
3.
ISR04 – Course Registration Card (One per course)
This contains information about
the student for each course he plans to take, it usually ends up with the
lecturer for that particular course.
4.
SRO01 – Basic Student Bio-Data Form (1 copy)
This contains basic information
about the student and is very similar to MIS01. Most of the information on this
form is found on MIS01.
5.
IFE FORM ADM ‘A’ (2 copies)
This form is filled after
verification of certificates. It is basically a letter stating that the student
is qualified for admission into the university. One copy (white copy) is
forwarded to the Director, Academic Affairs, while one copy (blue copy) is
retained by the dean of the faculty.
6.
IFE FORM ADM ‘C” (3 copies)
This form also verifies that the
student is qualified for admission and can now pay the prescribed fees. When
signed by the bursar, the white copy is retained by him, the blue copy is
forwarded to the admissions office while the yellow copy is produced during
registration for courses.
7.
IFE FORM ADM ‘D’ (1 copy)
This form shows, once again,
that the student is qualified for admission. It is for the Director, Student
Affairs.
8.
IFE FORM ADM ‘E’ (1 copy)
This form also verifies that the
student is qualified for admission. It however, allows the student to register
in the health centre.
Forms MIS01, ISRO4, SRO1, ADM FORMS ‘D’ and ‘E’
all require passport photographs.
We hope to:
1.
Solve the
problem of duplication by filling out one HTML form and having the information
distributed around to the various units.
2.
Merge certain
similar forms e.g. MIS01 and SRO1
3.
Simplify the
process of going to various points by using just a spot for the filling out of
forms. The only things that still need to be done physically are medical
check-up and verification of certificates.
CHAPTER 2: Literature Review
Two programming languages, HTML
(Hyper Text Markup Language) and Java, were used in the project.
2.1 HTML (Hyper
Text Markup Language)
Hypertext
Markup Language (HTML) is the standard text-formatting language since
1989 for documents on the interconnected computing network known as the World
Wide Web. HTML documents are text files that contain two parts: content that is
meant to be rendered on a computer screen; and markup or tags, encoded
information that directs the text format on the screen and is generally hidden
from the user. HTML is a subset of a broader language called Standard
Generalized Markup Language (SGML), which is a system for encoding and
formatting documents, whether for output to a computer screen or to paper.
Some tags in an HTML document determine the way
certain text, such as titles, will be formatted. Other tags cue the computer to
respond to the user's actions on the keyboard or mouse. For instance, the user
might click on an icon (a picture that represents a specific command), and that
action might call another piece of software to display a graphic, play a
recording, or run a short movie. Another important tag is a link, which may
contain the Uniform Resource Locator (URL) of another document. The URL can
be compared to an address where a particular document resides. The document may
be stored on the same computer as the parent document or on any computer
connected to the World Wide Web. The user can navigate from document to
document simply by clicking on these links. HTML also includes markups for
forms, that let the user fill out information and electronically send, or
e-mail, the data to the document author, initiate sophisticated searches of
information on the Internet, or order goods and services.
The software that permits the user to navigate
the World Wide Web and view HTML-encoded documents is called a browser. It
interprets the HTML tags in a document and formats the content for screen
display. Since HTML is an accepted standard, anyone can build a browser without
concerning themselves with what form various documents will assume, unlike
documents produced by typical word processors, which must be translated into a
different format if another word processing application is used. Most sites on
the World Wide Web adhere to HTML standards and, because HTML is easy to use,
the World Wide Web has grown rapidly. HTML continues to evolve, however, so
browsers must be upgraded regularly to meet the revised standards. The current
version of HTML is HTML 4.0 .
2.1.1 Features
of HTML 4.0
2.1.1.1 Frames
One of the biggest improvements in the latest
version of HTML is the specification's recognition of both standard and in-line
frames. Frames aren't new, of course. In fact, standard frames were originally
introduced by Netscape Navigator 2.0, and various browser versions have
introduced enhancements ever since. Fortunately, to be HTML 4.0-compliant,
browsers will have to support frames as defined in the specification.
With standard frames, you create Web pages with
miniwindows that each contain separate content. Normally, each miniwindow is
separated by a distinct border and displayed with scroll bars. You can also
insert a frame directly into a block of text on a Web page, much as you might
insert an in-line image. This is known as an in-line frame, and is created
using the iframe tag. In-line frames have many of the same attributes as
standard frames and others have been added for sizing and aligning the frame
window.
To use an in-line frame, choose where you want to
insert it, and then add the iframe element. You specify a source document with
the src attribute and then size and position the frame. The following example
inserts a 500-pixel-high by 325-pixel-wide in-line frame:
<iframe src="samples.htm" width="325"
height="500" align="right"></iframe>
As with standard frames, you can design the
in-line frames without borders using the frameborder attribute. You set the
attribute value to 1 to display the border or 0 to hide it. To achieve the
desired effect, you need to ensure that the contents of the source document fit
within the frame. Otherwise, the browser will display a border and scroll bars
for the frame.
Note that the iframe tag allows you to define
information to display in browsers that aren't HTML 4.0-compliant. Just place
the information within the iframe element like this:
<iframe src="samples.htm" width="325"
height="500" frameborder="0">
<P>Normally, a product sample is displayed in this space. However, your
browser doesn't support HTML 4.0.</P>
</iframe>
Compliant
browsers will ignore text placed like this, while noncompliant browsers will
ignore the iframe tag and display the information.
One
more thing to note about in-line frames: If you name the frame, you can create
links that display other files in the frame. The process of directing a
hyperlink to a frame is called targeting. You target an in-line frame using the
value of its name attribute. Simply assign the name as the value of the target
attribute for the associated hyperlink. Figure 1 shows an example of this. The
in-line frame is named samp. Three links in the example use this name to target
the frame. When you click on a link, the related source file is loaded into the
frame.
EXAMPLE 1: Target in-line frames using the name attribute's value.
<HTML><HEAD><TITLE>Inline Frames Example</TITLE></HEAD><BODY BGCOLOR="#FFFFFF"><DIV><H1 align="center">Calculators R Us</H1><IFRAME name="samp" src="samples.htm" width="325" height="500" align="right" frameborder="0"></IFRAME>Our catalog features over 500 products that you cansample online. We invite you to try the product demosand stay awhile. Today's featured product is 25% off.See other featured products by selecting them.</P> <A href="feature1.htm" target="samp"> S5000 Scientific Plus</A> <BR><A href="feature2.htm" target="samp"> E2800 Engineering Max</A> <BR><A href="feature3.htm" target="samp"> M3500 Statistical Plus</A></P></DIV></BODY></HTML>
2.1.1.2 Mulimedia
Another major step forward is the adoption of the
object element, which provides a general-purpose tag for working with different
types of media such as Java applets, in-line video, streaming audio, and
images. Thus it should eventually replace the various tags for different media
types. Instead of using applet, img, and embed, you'll simply use object.
The object element can even be used to display
text-based files in a browser window, acting in this case much like an in-line
frame. Originally, object was proposed as a compromise to using tags designed
for a specific purpose like img and applet. Unfortunately, although browser
developers saw the need for a standard way to include multimedia in Web pages,
they didn't necessarily agree on a way to do this. And so the object tag did
not become part of the official HTML specification for some time. Finally, with
HTML 4.0, the object element is being recognized as the solution to the future
of embedded multimedia in Web pages.
HTML 4.0-compliant browsers will have no problem
interpreting <object> tags, but older browsers may not fare so well, and
as a result won't know how to display and run your embedded multimedia. For
backward compatibility, you may want to insert media-specific tags within the
object element. Be sure that these tags immediately follow the first
<object> tag. In the following example, if the browser can't understand
the <object> tag it will try to use the <embed> tag:
<object data="cougar.bmp" type="image/bmp"><embed src="cougar.bmp"></object>
2.1.1.3 Tables
Most of the table innovations in HTML 3.0 remain intact in HTML
4.0, and there are new features as well. You can now group columns together and
define column properties at the beginning of the table. You can also define
header, footer, and body sections for tables.
You define individual header or data cells with the th and td
elements, and you tell browsers what columns in the table look like using two
elements: The colgroup tag creates a structural grouping that sets the
characteristics of columns within the group, and col shares attributes within
this structure. Together, these elements allow browsers to start displaying
table columns immediately and to build the table incrementally as it is being
downloaded.
Using these new elements in a table is easier than you may think.
The elements support an identical set of attributes, which gives you a great degree
of freedom in defining group structures. The width, cellhalign, and cellvalign
attributes set the default column width, horizontal cell alignment, and
vertical cell alignment respectively, and span sets the number of columns that
share an element's attributes. You can also use attributes for style sheets and
intrinsic events to make your tables more dynamic.
Example 2 shows how these attributes can be used in a table, we see
several different ways to set the structure for an identical group of columns.
Note that if you use relative widths for columns instead of defining absolute
widths in pixels, you will need to set the entire table width using the table
element's width attribute.
You can group table rows into header, footer, and body sections
using the thead, tfoot, and tbody elements. The header and footer contain
information about the table's columns and the table body contains rows of table
data. Ideally, browsers will use this separation to display tables
intelligently. For example, if the table extends beyond the current window, the
browser could allow the reader to scroll through the body of the table while
the header and footer sections remain on the screen. Or when a large table is
being printed, the browser could include the header and footer sections on each
page of the document.
These elements are easy to use. You insert the header and footer
sections into the beginning of the table and then define the body sections.
Header and footer sections come first so that browsers can display the table
even if the body sections are still being retrieved. Example 3 defines a
standard header and footer for a table. Note that the end tags are used for
table headers, footers and body sections even though they aren't required in
the specification.
EXAMPLE 2: Using the COLGROUP and COL elements.
//Setting the width of each
column individually
<COLGROUP><COL width="100"><COL width="100"><COL width="100"><COL width="75"><COL width="75"><COL width="75"></COLGROUP>
//Using spans to make the
code more compact
<COLGROUP><COL span="3" width="100"><COL span="3" width="75"></COLGROUP>//Assigning the column width and span directly to the column groups<COLGROUP span="3" width="100"></COLGROUP><COLGROUP span="3" width="75"></COLGROUP>
EXAMPLE 3: Use headers and footers to help the browser structure
the table.
<TABLE BORDER=2 WIDTH=50%><COLGROUP><COL width="100"><COL width="75"><COL width="75"><COL width="75"></COLGROUP><THEAD><TR> <TH> </TH> <TH>1996</TH> <TH>1997</TH> <TH>1998</TH> </TR></THEAD><TFOOT><TR><TD>Company data provided for statistical purposes only.</TD></TR></TFOOT><TBODY><TR> <TH>Week 1</TH> <TD>252</TD> <TD>267</TD> <TD>289</TD> </TR><TR> <TH>Week 2</TH> <TD>194</TD> <TD>197</TD> <TD>205</TD> </TR><TR> <TH>Week 3</TH> <TD>212</TD> <TD>225</TD> <TD>234</TD> </TR><TR> <TH>Week 4</TH> <TD>145</TD> <TD>176</TD> <TD>179</TD> </TR><TR> <TH>Week 5</TH> <TD>167</TD> <TD>182</TD> <TD>193</TD> </TR><TR> <TH>Week 6</TH> <TD>185</TD> <TD>201</TD> <TD>205</TD> </TR><TR> <TH>Week 7</TH> <TD>197</TD> <TD>207</TD> <TD>213</TD> </TR>. . .<TR> <TH>Week 52</TH> <TD>203</TD> <TD>221</TD> <TD>279</TD> </TR></TBODY></TABLE>
2.1.1.4 Forms
Forms haven't changed much since they were introduced in previous
versions of HTML. This is unfortunate, because forms aren't entirely
user-friendly and have needed improvements for a long time. This time around,
however, the HTML specification addresses some of the most obvious
shortcomings.
There are many new features for forms, but let's focus on some of
the most useful: tab indexes and access keys. With tab indexes, you can provide
a way for users to navigate easily through form fields with a keyboard. You do
this by specifying the tabbing order for each element in the form, which makes
it possible to use the Tab key to move back and forth through form fields. In
the following example, the tabbing order is set sequentially with the tabindex
attribute.
<form action="cgi-bin/data.pl" method="post"><P>Name: <input tabindex="1" type="text" name="userName"></P><P>Email: <input tabindex="2" type="text" name="userEmail"></P><P>Phone: <input tabindex="3" type="text" name="userPhone"></P><P><input tabindex="4" type="submit"><input tabindex="5" type="reset"></P></form>
When the user presses Tab,
the userName field will be accessed first, the userEmail field next, and so on.
The tabbing order can include any number from 0 to 32,767. Browsers use the
numerical value to determine the next or previous field.
Form fields can also be assigned an access key. Access keys let you
use keyboard shortcuts for quick access to a specific field in a form. For
example, if you assigned the N key to the userName field in the previous
example, you would be able to use this key to go directly to the field. The way
access keys work depends on the operating system you are running. On Microsoft
Windows systems, you typically press the Alt key in addition to the access key.
Thus, to access the userName field on a Windows system, you'd press Alt-N.
Browsers should display the access key for an input field in some
unique way, such as with underlined or bold text. You can assign the access key
to a form field directly using the accesskey attribute, but you can help the
browser better determine how to render the access key by labeling your input
fields and assigning the access key to the label. Labels are new to HTML 4.0.
When you label a form field, you attach information to the field. Labels use a
for attribute to identify the related form field. The value of this attribute
must correspond to the value of an id attribute in the related field. The
following sample uses labels with text input fields:
<form action="cgi-bin/data.pl" method="post"><label for="name" accesskey="N">Name: </label><input id="name" type="text"><label for="email" accesskey="E">Email: </label><input id="email" type="text"><label for="phone" accesskey="P">Phone: </label><input id="phone" type="text"><P><input accesskey="S" type="submit"><input accesskey="R" type="reset"></P></form>
Another useful form enhancement is the button element. This element
creates a push button, much like the Reset and Submit buttons used in forms.
However, you can add content to these new buttons (something you couldn't do
with standard push buttons), so your new buttons can contain images, paragraphs
of text, and other extras.
To add these extras, all you need to do is insert them between the
opening <button> tag and the closing </button> tag. Thus, you could
replace the standard Submit and Reset buttons used in a previous example with
button elements. To make these elements stand out, you could add text and
images, such as
. . .<button tabindex="4" accesskey="S" name="submit" type="submit">Enter your name in the database! <img src="go.gif" alt="Submit it!"></button><button tabindex="5" accesskey="R" name="reset" type="reset">Start over! <img src="ohno.gif" alt="Try again!"></button>
Older browsers may not be
able to use the button element. Instead of a push button, you'll see only the
button's contents. A workaround is to place submit and reset fields within the
button element, such as
<button name="submit" type="submit"><input type="submit"></button><button name="reset" type="reset"><input type="reset"></button>
2.1.1.5 Scripting
Scripting is the key to interactivity on the Web. Until recently,
however, scripting mechanisms weren't well defined in the HTML specification,
leading to a lot of inconsistency in how browsers handled scripts. The good
news is that HTML 4.0 takes a more thorough approach.
One of the most important changes involves how you specify scripts
in your Web pages. With the meta element, you can now define a default
scripting language for all scripts in a page. You do this by specifying a value
for the Content-Script-Type HTTP header . If you do not assign a default value
in a <meta> tag, the browser can try to extract this value from the
associated field in the actual HTTP header sent by the Web server.
When you set a default scripting language, you use the MIME content
type for scripts. Most often, the MIME content type will be either
text/vbscript for VBScript or text/JavaScript for JavaScript, but other valid
content types can be used, such as text/tcl for TCL. To set the default
scripting language to JavaScript, you'd use
<meta
http-equiv="Content-Script-Type"
content="text/javascript">
You can override the default scripting language at any point in
your pages with the script element, but note that the specification no longer
recommends that you use the language attribute with it. Instead, the HTML
specification recommends that you use the type attribute, which lets you
specify the MIME content-type for your scripts, for example <script
type="text/vbscript">. But, if you use the type attribute, some
older browsers may not be able to handle your scripts properly. While all this
gets sorted out, it is probably a good idea to know that the type attribute is
valid but doesn't have to be used just yet.
Another important change for Web scripting is that most HTML
elements now support a wide range of event attributes. Events occur
automatically when a certain condition exists. Some events are user-driven, by
the press of a key or a click of the mouse. Others are browser-driven, such as
when the browser finishes loading an image. Event attributes allow you to
specify the conditions you want an element to detect. For example, you can
create clickable cells in tables, paragraphs of text that light up when the
mouse is over them, and a whole lot more.
There are several ways to work with events. You can use event
attributes, such as onclick or onkeypress, to detect the event and then pass it
off to a script function. On the other hand, if you want to check for a
specific event within your code, you can create a function to detect and handle
the event directly. The following example shows how you could use the
onmouseover event attribute with the <a> tag:
<href="main.htm"
onmouseover="show('Visit our home page')">Main</a>
When the mouse pointer is over the anchor text, the show() function
is called and passed the associated text. As you'll discover, the best time to
use event attributes in this way is when you want to use the same function
repeatedly.
Anytime you use events specific to HTML 4.0, it is a good idea to
test your page in a noncompliant browser. Generally, these browsers ignore
event attributes they don't understand, and as a result, the functionality you
expect won't be supported. If you plan your Web page with this in mind, you
should be able to avoid problems.
2.1.1.6 Style Sheets
When you want to create attractive Web pages, you'll find that
cascading style sheets provide the necessary ammunition. Style sheets let you
control the color of text and backgrounds, the positioning of content, and many
other crowd-pleasing extras. Before style sheets came along, Web publishers had
to rely on existing HTML structures to control the look and feel of their Web
pages. If you wanted to change a page's background color, you used the bgcolor
attribute of the body element. If you wanted to center text on the page, you
used the center element, and so on.
Unfortunately, when you mix a document's presentation information
with its content, you create a document that is unnecessarily complex and
difficult to maintain. Because style sheets offer a way to separate the
presentation of documents from the actual content, there is a major initiative
to phase out most of the presentation elements and attributes from HTML. Keep
in mind, however, that change takes time; it will likely be a while before
these elements and attributes are completely removed.
Elements and attributes that are in danger of being dropped from
the HTML specification are designated as deprecated (disapproved for use). One
of the elements many Web publishers will miss is font, which is used to specify
text color, font face, and font size. Other elements on the chopping block
include: basefont, which is used to set default font information; center, used
to center elements on the page; and a few other elements such as u for
underlining and s for strikethrough text.
In addition to placing elements on the disapproved list, the
specification declares some elements obsolete and others as not recommended for
use. Obsolete elements are no longer listed in the HTML specification and there
is no guarantee a browser will support them. Although it is very clear that you
shouldn't use obsolete elements, elements not recommended for use are in a kind
of nether realm. They aren't on the deprecated list, they aren't obsolete, and
you aren't encouraged to use them either.
Obsolete elements include listing for code listings, plaintext for
plain text listings, and xmp for examples. Instead of using these elements, you
should use the pre element, which allows the use of preformatted text.
Elements not recommended for use are big for large text, small for
small text, tt for monospaced text, i for italic, and b for bold. Although
these elements aren't on the disapproved list, you are encouraged to use style
sheets instead.
The list of deprecated attributes is substantial. For example, with
the body tag, the background, bgcolor, link, text, alink, and vlink attributes
are all on the hit list. Other deprecated attributes include border for images
and objects, clear for line breaks, and noshade for horizontal rules; the list goes
on and on. Remember, if you use an attribute for presentation, you're probably
better off using a style sheet to control it.
2.1.1.7 Document Type Definitions
The developers of HTML thought about the issue of element and
attribute support when you take a look at the DTDs for HTML 4.0. A DTD
(document type definition) sets the rules and defines the structures you can
use in compliant documents. HTML 4.0 defines three DTDs: a strict DTD, a loose
DTD, and a frameset DTD.
The HTML 4.0 specification states that you must specify one of
these DTDs in your Web pages. You specify the DTD by placing the document type
declaration as the first line of the Web page. If you choose not to specify the
DTD, be forewarned that the strict version is the one compliant browsers are
supposed to use by default.
A key goal of the strict DTD is to enforce the separation of visual
formatting from the actual content. You do this by using style sheets to
control the presentation of your Web pages. Because of this, the strict DTD
does not include any deprecated elements or attributes, or any structures used
for frames. As you can see, this is the most restrictive DTD. If you have an
HTML 4.0-compliant browser and you want to test your Web page with the strict
DTD, you can use the following document type declaration:
<!doctype HTML public"-//W3C//DTD HTML 4.0//EN""http://www.w3.org/TR/REC-html40/strict.dtd">
The loose DTD doesn't restrict the elements and attributes used for
presentation. Because this DTD is regarded as an interim stage, it is also
referred to as the transitional DTD. As you might expect, you can use any of
the deprecated elements and attributes with this DTD. Use the following
declaration to test a page with the transitional DTD:
<!doctype HTML public "-//W3C//DTD HTML 4.0 Transitional//EN" "http://www.w3.org/TR/REC-html40/loose.dtd">
The final DTD is designed for frame-enhanced Web pages. This
version supports all the structures in the loose DTD as well as the structures
needed for frames. To specify this DTD, use this declaration:
<!doctype HTML public "-//W3C//DTD HTML 4.0 Frameset//EN" "http://www.w3.org/TR/REC-html40/frameset.dtd">
2.1.2 Writing
HTML programs
HTML
programs are written with text editors, especially notepad, which is the
default text editor that comes with all versions of Microsoft Windows. The
code, after being written out, is saved in the following form:
“sowande.htm”
After
this, the default browser is used to view the web page.
2.2
Object-Oriented Programming: Java
In
order to use Java, one has to understand the concept of object oriented
programming, popularly called OOP.
Object
oriented software is all about objects. An object is a “black
box”, which receives and sends
messages. A black box actually contains code(sequences of computer
instructions) and data(information which the instructions operate on).
Traditionally, code and data have kept apart. For example, in the C language,
units of code are called functions, while units of data are called structures.
Functions and structures. Functions and structures are not formally connected
in C. A C function can operate on more than one type of structure, and more
than one function can operate on the same structure.
This
is not the case in object-oriented programming. In object-oriented programming,
code and data are merged into a single indivisible thing – an object. This has
some big advantages. A primary rule of object-oriented programming is this: as
the user of an user of an object, you
should never need to know what is inside the box.
All
communication is done via messages. The object, which a message is sent to, is the receiver
of the message. Messages define the interface to the object. Everything an
object can do is represented by its message interface. So you shouldn’t have to
know anything about what is in the black box in order to use it.
Not
looking inside the object in the black box doesn’t tempt you to directly modify
that object. If you did, you would be tampering with the details of how the
object works. Suppose the person who programmed the object in the first place
decided later on to change some of the details? Then you would be in trouble,
your software would no longer work correctly. But as long as you just deal with
objects as black boxes via their messages, the software is guaranteed to work.
Providing access to an object only through its messages, while keeping the
details private is called information
hiding or encapsulation.
Why
all this concern for being able to change software? Because experince has taught
us that software changes. A popular adage is that “software is not written, it
is re-written”. And some of the costliest mistakes in computer history have
come from software that breaks when someone tries to change it.
2.2.1 Classes
How
are object defined? An object is defined via its class, which determines
everything about an object. Objects are individual instances of a class. For
example, you may create an object called Bingo from class Dog. The Dog class defines what is to be a Dog object can act upon.
All object-oriented languages have some means, usually called a factory,
to “manufacture” object instances from a class definition.
You
make more than one object of this class, and call them Bingo, Fido, Rover, etc.
The Dog class defines messages that Dog objects understand, such as “bark,
“fetch” and “roll-over”.
You
may also hear the term method used. A method is simply the action that a message carries out. It
is the code, which gets executed when the message is sent to a particular
object.
Arguments
are often supplied as part of a message. For example, the “fetch” message might
contain an argument that says what to fetch, like “the-stick”. Or the
“roll-over” message could contain one argument to say how fast, and a second
argument to say how many times.
2.2.1.1
Examples
If
you wanted to add two numbers, say, 1 and 2, in an ordinary,
non-objected-oriented computer language like C, you might write this:
a=1;
b=2;
c=a+b;
This says,
“Take a, which
has the value 1, and b, which has the value 2, and add them together using the
C language’s built-in addition capability. Take the result, 3, and place it
into the variable called c.”
Now, here’s the came thing expressed in
Smalltalk, which is a pure object-oriented language:
a : =1.
b
: = 2.
c
: = a + b.
This looks almost exactly the same,
but the meaning is dramatically different.
In Smalltalk, this says,
“Take the
object a, which has the value 1, and send it the message “+”, which included the argument b, which, in
turn, has the value 2. Object a, receive this message and perform the action
requested, which is to add the value of the argument to yourself. Create a new
object, give this the result, 3, and assign this object to c.”
This seems like a far more complicated way of accomplishing
exactly the same thing. However, objects greatly simplify matters when the data
gets more complex. Suppose you wanted a data type called list, which is a list
of names. In C, list would be defined as a structure.
Struct list {
<definition of list structure data here>
} ;
list a,b,c;
a = “Olubunmi Sowande”;
b = “Gbenga Sesan”;
In C, you cannot perform the
following command:
c = a + b;
The C compiler
will generate an error, because it doesn’t know what to do with a and b. C compilers just know how to add numbers. One can do the same
thing in Smalltalk, but this time, list is made a class, which is a subclass of
the built-in Smalltalk class called “String”:
a : = List fromString: ‘Olubunmi Sowande’.
b : = List fromString: ‘Gbenga Sesan’.
c : = a + b
The first two lines simply create List objects a and b from the given strings. This now works, because the list class
was created with a method which specifically “knows” how to handle the message
“+”. For example, it might simply combine the argument with its own object by
sticking them together with comma separating them (this is done with a single
line of Smalltalk). So c will have
the new value:
‘Olubunmi Sowande ,Gbenga Sesan’
2.2.2 Using
Non-Object-Oriented Languages
It’s also possible to use objects
and messages in plain old non-object-oriented languages. This is done via
function calls, which look ordinary, but which have object-oriented machinery
behind them. Among other things, this allows sophisticated client-server
software to run “transparently” from within ordinary programming languages.
Suppose you added a “plus” function
to a C program:
int plus(int arg1, int arg2)
{return
(arg1 + arg2);}
This hasn’t really brought you
anything yet. But suppose that instead of doing the addition on you own
computer, you automatically sent it to a server computer to be performed:
int plus(int arg1, int arg2)
{return server_plus(arg1, arg2);}
The function
server_plus() in turn creates a message containing ar1 and arg2, and send this
message, via a network, to a special object which sits on a server computer.
This object executes the “plus” function and sends the result back to you. It’s
object-oriented programming via a ‘back-door’ approach.
This example is not very fancy, and of course,
it’s easier to simply add two numbers directly. But, there’s no limit to the
complexity of an object. A single object can include entire databases, with
millions of pieces of information. In fact, such database objects are common in
client-server software.
This
also illustrates the flexibility of the object-oriented approach. In the usage just described, the object is
very different from the earlier “a + b” example. Here, it receives two
arguments, namely, the two objects it was supposed to add. Previously, in the
Smalltalk example, the object that was receiving a message was the first
object, a. But in a client-server
environment, the addition is not done locally, on the client machine, but
remotely, on a server machine. The server machine contains the object that the
message is sent to, and since it doesn’t how anything about the forst argument,
you have to send both arguments.
2.2.3 Inheritance
If
there is already a class which can respond to a group of different messages,
what if you wanted to make a new, similar class which adds just a couple of
more messages? Why have to rewrite the whole class?
Of
course, in any good object-oriented language, you don’t. All you need to do is
create a subclass (or derived
class, in C++ terminology) of the original class. This new class inherits all the existing messages, and
therefore, all the behaviour of the original class. The original class is
called the parent class, or superclass,
of the new class. A subclass is said to a specialization
of its superclass, and the conversely a superclass a generalization of its subclasses.
Inheritance also promotes reuse. You don’t have
to start from scratch when you write a new program. You can simply reuse an
existing repertoire of classes that have behaviours similar to what you need in
the new program.
For example, after creating the class Dog, you might make a subclass called Wolf, which defines some wolf-specific
messages such as hunt. Or it might
make more sense to define a common class called Canis, of which Dog and Wolf are subclasses.
Much of the art of object-oriented programming is
determining the best way to divide a program into an economical set of classes.
In addition to speeding up development time, proper class construction and
reuse results in far fewer lines opf code, which translates to less bugs
(errors) and lower maintenance costs.
2.2.4 Object Oriented Languages
There
are almost two dozen major object-oriented languages in use today. But the
leading commercial object-oriented languages are far fewer in number. They are:
·
C++
·
Smalltalk
·
Java
2.2.4.1 C++
C++
is an object oriented version of C. It is compatible with C (it is actually a
superset), so that existing C code can be incorporated in C++ programs. C++
programs are fast and efficient, qualities which helped make C an extremely
popular programming language. It sacrifices some flexibility in order to remain
efficient, however, C++ uses compile-time
binding, which means that the programmer must specify the specific class of
an object, or at the very least, the most general class that an object can
belong to. This makes for high run-time efficiency and small code size, but it
trades off some of the power to reuse classes.
C++ has become so popular that most new C
compilers are actually C/C++ compilers. However, to take full advantage of
object-oriented programming, one must program (and think) in C++, not C. This
can often be a major problem for experienced C programmers. Many programmers
think they are coding in C++, but instead are only using a small part of the
languages object-oriented power.
2.2.4.2
Smalltalk
Smalltalk
is a pure object-oriented language. While C++ makes some practical compromises
to ensure fast execution and small code size, Smalltalk makes none. It uses run-time
binding, which means that
nothing about the type of object needs to be known before a Smalltalk program
is run.
Smalltalk programs are considered by most to be
significantly faster to develop than C++ programs. A rich class library that
can be easily reused via inheritance is one reason for this. Another reason is
Smalltalk’s dynamic development environment. It is not explicitly compiled,
like C++. This makes the development process more fluid, so that “what if”
scenarios can be easily tried out, and class definitions easily refined. But
being purely object-oriented, programmers cannot simply put their toes into the
object-oriented waters, as with C++. For this reason, Smalltalk generally takes
longer to master than C++. But most of the time is actually spent learning
object-oriented techniques, rather than the details of a particular programming
language. In fact, Smalltalk is syntactically very simple, much more than
either C or C++.
Unlike C++, which has become standardized, the
Smalltalk language differs somewhat from one implementation to another. The
most popular “dialects” of Smalltalk are:
·
VisualWorks from ParcPlace-Digitalk, Inc.
·
Smalltalk/V and
Visual Smalltalk from ParcPlace-Digitalk,
Inc.
·
VisualAge from IBM
2.2.4.2.1 VisualWorks
VisualWorks
is arguably the most powerful of Smalltalks. VisualWorks was developed by
ParcPlace, which grew out of the original Xerox PARC project that invented the
Smalltalk language. VisualWorks is platform-independent, so that an application
written under one operating system, say, Microsoft Windows, can work without
any modification on any of a wide range of platforms supported by ParcPlace,
from Sun Solaris to Macintosh. VisualWorks also features a GUI (Grpahic User Interface) builder that is well integrated into
the product.
2.2.4.2.2 Smalltalk/V and Visual Smalltalk
Digitalk’s
versions of Smalltalk are somewhat smaller and simpler, and specifically
tailored to IBM compatible PCs. A Macintosh version was available, but support
has since been abandoned. This does not bode well for Digitalk cross-platform
efforts. Digitalk has a separate GUI builder, called PARTS Workbench (bundled
with Visual Smalltalk), which allows quick construction of an application.
ParcPalce and Digitalk were merged into a single
company, ParcPlace-Digitalk, Inc. The
future of the Digitalk product line is uncertain, and it may just be spun off
back into a separate company.
2.2.4.2.3 VisualAge
IBM’s
version of Smalltalk, VisualAge, is comparable to Smalltalk/V with PARTS. Both
of these Smalltalks allow programmers to readily exploit machine-specific
features, at the expense of some portability. IBM has adapted existing industry
standards for such things as file management and screen graphics. When IBM
talks, people listen, and IBM has made a substantial commitment to Smalltalk.
2.2.4.2.4 Java
This
is the latest, flashiest object-oriented language. It has taken the software
world by storm due to its close ties with the Internet and Web browsers. It is
designed as a portable language that can run on any web-enabled computer via
that computer’s Web browser. As such, it offers great promise as the standard
Internet and Intranet programming language.
Java is a curious mixture of C++ and Smalltalk.
It has the syntax of C++, making it easy (or difficult) to learn, depending on
your experience. But it has improved on C++ in some important areas. For one
thing, it has no pointers; low-level programming constructs that make for
error-prone programs. Like Smalltalk, it has garbage collection, a feature that frees the programmer from
explicitly allocating and de-allocating memory. And it runs on a
Smalltalk-style virtual machine, software built into your web browser which
executes the same standard compiled Java bytecodes no matter what type of computer you have.
Java Development tools are being rapidly
deployed, and are available from such major software companies as IBM,
Microsoft, Borland and Symantec.
Object-oriented
programming offers a new and powerful model for writing computer software.
Objects are “black boxes” which send and receive messages. This approach speed
the development of new programs, and, if properly used, improves the
maintenance, reusability, and modifiability of software.
Object-oriented programming requires a major
shift in thinking by programmers, however. The C++ language offers an easier
transition via C, but it still requires and object-oriented design approach in
order to make proper use of this technology. Smalltalk offers a pure
object-oriented environment, with more rapid development time and greater
flexibility and power. Java promises much for Web-enabling object-oriented
programs.
2.3 Java – the programming language
The
primary need for Java is for developing software over networks. It works
consistently, anywhere, on any platform – and interacts with other
applications. It can access disparate and distributed information sources, and
can be extended and upgraded seamlessly. In summary, it is a
machine-independent programming language that is both safe to traverse networks
and powerful enough to replace native executable code.
Java is a network programming language that was
developed by Sun Microsystems. It’s already in widespread use for creating
animated and interactive web pages. However, it is rich enough to support entirely
new kinds of applications, like dynamically extensible browsers and mobile
agents. There are entirely new kinds of computer platforms that are being
developed around Java (handheld devices and network computers) that download
all their software over the network.
Sun and other industry giants are fast producing
Java chips and microprocessors tailored to run media-rich Java applications.
Hardware implementations of Java could power inexpensive network terminals,
PDAs (Personal Digital Assistants)
and other information appliances, to take advantage of transportable Java
applications. Software implementations of Java are available now for portable
computing devices like the popular PalmTM PDA. We could soon have
Java applets running on wristwatches! You can already get “smart cards” and
“wearable” devices like rings and dog-tags that have Java interpreters embedded
in them. These devices are capable of doing everything from financial
transactions (paying a hotel bill) to unlocking a door (the door to your hotel
room) to rerouting phone calls (so your hotel room receives your business
calls). The hardware is already there; it can’t belong before the rest of the
software infrastructure begins to take advantage of it. A Java wristwatch is
not a silly notion.
2.3.1 A Virtual Machine
Java
is both a compiled and interpreted language. Java source code is turned into
simple binary instructions, much like ordinary microprocessor code. However,
whereas C or C++ source is refined to native instructions for a particular
model of processor, Java source is compiled into a universal format –
instructions for a virtual machine.
Compiled Java byte-code, called J-code,
is executed by a Java runtime interpreter. The runtime system performs
all the normal activities of a real processor, but it does so in a safe,
virtual environment. It executes the stack-based instruction set and manages a
storage heap. It creates and manipulates primitive data types, and loads and
invokes newly referenced blocks of code. Most importantly, it does all this in
accordance with a strictly defined open specification that can be implemented
by anyone who wants to produce a Java-compliant virtual machine. Together, the
virtual machine and language and definition provide a complete specification. There
are no features of Java left undefined or implementation-dependent. For
example, Java specifies the sizes of all its primitive data types, rather than
leave it up to each implementation.
The Java interpreter is relatively lightweight
and small; it can be implemented in whatever form is desirable for a particular
platform. On most systems, the interpreter is written in a fast, natively
compiled language like C or C++. The interpreter can be run as a separate
application, or it can be embedded in another piece of software, such as a web
browser.
All of this means that Java code is implicitly
portable. The same Java application byte-code can run on any platform that
provides a Java runtime environment, as shown in the diagram below. You don’t
have to produce alternative versions of your application for different
platforms, and don’t have to distribute source code to end users.
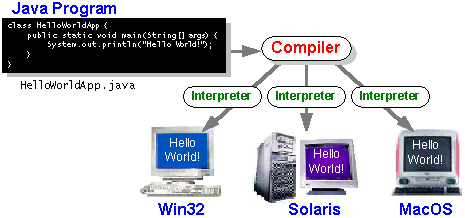
Figure 2.1 Portability
of Java Source Code
The fundamental unit of Java code is the class.
As in other object-oriented languages, classes are application components that
hold executable code and data. Compiled Java classes are distributed in a
universal binary format that contains Java byte-code and other class
information. Classes can be maintained discretely and stored in files or
archives on a local system or on a network server. Classes are located and
loaded dynamically at runtime, as they are needed by an application.
Java also has some fundamental classes that
contain architecture-dependent methods, called native methods. They
serve as a gateway between the Java virtual machine and the real world. They
are implemented in a natively compiled language on the host platform, providing
access to resources such as the network, the windowing system and the host file
system. The rest of Java is written entirely in Java, and is therefore
portable, including the Java compiler and HotJava web browser.
Java is a relatively fast interpreted language,
as it runs compiled byte-code. It has also
been designed do that software implementations of the runtime system can
optimise their performance by compiling byte-code to native machine-code on the
fly, a process called just-in-time compilation. However,
array bounds checking will always reduce the performance of Java, but this is
for the sake of security.
The latest compilation technique is a new virtual
machine that Sun calls HotSpot. It measures (profiles) the code as it is
executing, to see which parts are being executed repeatedly. Once it knows
which parts of code are crucial to the performance, HotSpot compiles those
sections – and only those sections – into true machine code, it can afford to
take the time necessary to optimise those portions. The rest of the program may
not need to be compiled at all- just interpreted –saving memory and time.
2.3.2 Java compared with other languages
Java
is extremely similar to C or C++ when it comes to syntax, but the similarities
end there. C trades functionality for portability, Java trades speed for
portability. Java also addresses security issues, while C doesn’t. As an
interpreted language, it can’t be as fast as a compiled language, but it is
fast enough for interactive network-based applications, where the application
is often idle, waiting for the user to do something or waiting for data from
the network. For situations where speed is critical, just-in-time compilation
can be used.
Scripting languages like Perl, Python Tcl/Tk are
suitable for safe, networked applications but they are not designed for
serious, large-scale programming. They are rather casual about program
structure and data typing. However, they are dynamic; they provide powerful
tools for text-processing tasks that more general-purpose languages find
unwieldy, they are powerful tools for rapid prototyping and are also highly
portable. Java offers some of the essential advantages of a scripting language,
along with the benefits of a low-level language.
Incremental development with object-oriented
components, combined with Java’s simplicity, make it possible to develop applications
rapidly and change them easily, with a short concept-to-implementation time.
Java also covers with a large base of core classes for common classes for
common tasks such as building GUIs (Graphical User Interfaces) and doing
network communications. But along with these features, Java has the scalability
and software-engineering advantages of static languages. It provides a safe
structure on which to build higher networked tools and languages.
2.4 The Hardware Aspect – The OAU computer network
For the software to work efficiently,
the environment that the program will run in must be fully studied. Up to two
thousand people may be using the network at any given time, so we need to
ensure that the network is completely optimised for this purpose and eliminate
possible bottlenecks.
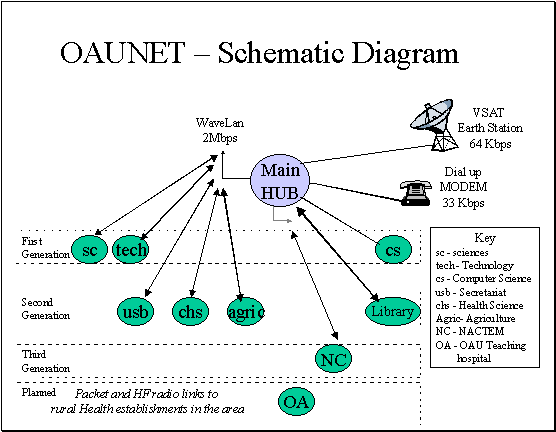
Figure 2.2 The OAU computer network - a
schematic diagram showing the location of all the servers
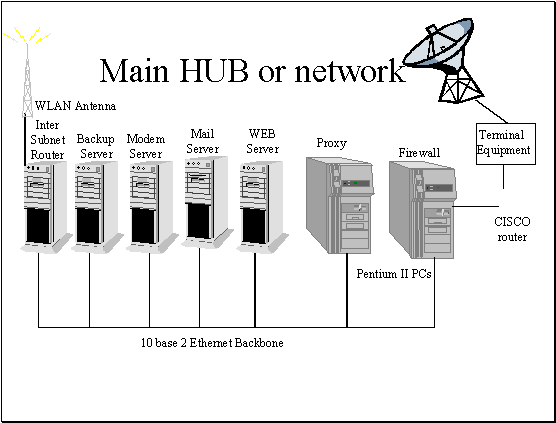
Figure 2.3 The main hub of the OAU
computer network located at the computer building
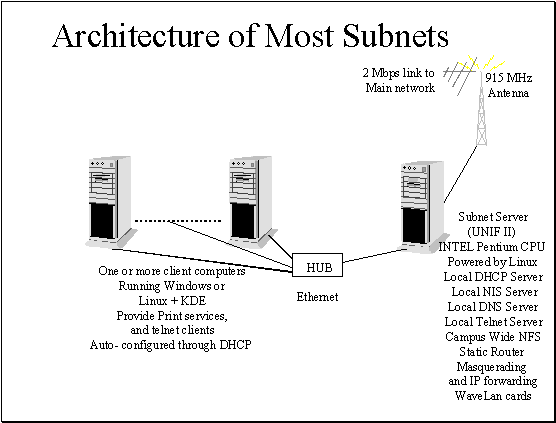
Figure 2.4 The
architecture of most subnets and the servers available
The diagrams above give a very detailed description of the school network. In
summary the network is as described below:
2.4.1 Servers
The typical server configuration on the network
is
·
Pentium II MMX 400
MHz
·
128MB RAM
·
8.4 GB HDD (several
instances of this may be available)
·
CD-Rom Drive (50
Speed)
2.4.2
Location
The
central server is located at the computer building, while the other servers are
located in:
·
Faculty of Science
(White House)
·
Faculty of
Agriculture
·
School Library
·
Secretariat (Senate
Building)
·
Health Sciences
Building
·
Centre for Energy
Research and Development / NACETEM
·
Faculty of
Technology (Civil Engineering Building)
The main function of these servers is to provide
authentication services for users located in these areas.`
2.4.3
Transmission
Communication
between each server location and the others is FULL DUPLEX – it
transmits and receives from both ends at the same time. The transmitters in the
non-central locations are unidirectional. The central
transmitter is omnidirectional and communicates by creating a circular
waveform that is received by each receiver.
The
university telephone exchange, that caters for internal communications, is
employed in the University network. It connects individuals and corporate
bodies through dial-up networks; e.g. Chemical Engineering, Pharmacy, Space
Research, etc.
The
NITEL exchange for ‘individual’ external communicates also, through a modem,
helps link individuals in staff quarters, town and even Ibadan, to the OAU
network.
2.4.3.1 Proactive Network Management
The
school network spans over several servers placed in key positions all over the
campus. Due to the rapid expansion of the network over the last two years, the
network has become increasingly slow, this is especially noticed when you try
to access the Internet.
The
program we are developing will run as a network application, therefore we have
to anticipate the effect of running the program on the network. There are
seventeen servers on our proposed network, and it is expected that up to 100
people could be using the program at 11 of these sites and about 20 people at
the remaining six sites, all at the same time, making a total of 1,220 people
using the network at peak periods of the day. This will mean efficient network
management, both before the deployment of the program and after.
There are two approaches to network management:
reactive and proactive solutions. Reactive solutions are what is found commonly
in Nigeria today, users complain about network problems, these problems, those
problems are fixed, and then users complain about new problems. This leads to a
seemingly endless cycle, and the result is that morale suffers, productivity is
slowed, and most importantly, users eventually learn to distrust the network.
Proactive strategies involve anticipation of
problems and minimizing their impact ahead of time. These strategies include
regular network baselining, proactive testing and building network testbeds.
You detect minor problems before they become major failures. We are deploying a
proactive solution to the deployment of our program to anticipate the impact on
the network. We will study certain scenarios where similar problems to the ones
we anicipate to face have occurred and how they were solved.
Some tools used in the process of network
baselining and testing are described below:
2.4.3.1.1
Advanced Cable Testers
Advanced
cable testers work beyond the lower levels of the OSI model to give real
insight into how the network is functioning. They display all sorts of
information, including:
·
Frame Counts
·
Congestion errors
·
Network Utilization
·
Late Collisions
·
CRC errors
·
Network-level
statistics
·
Protocol Statistics
·
Information
concerning which applications are using the network
By using the statistics, you can watch for
network errors such as collisions caused by excessive cable length or congestion
errors due to an overloaded segment. Normally, problems resulting from these
statistics are segment- or network-wide and affect all users.
An example can be found at www.fluke.com
2.4.3.1.2
Network Monitors
Network
monitors are software programs that track and show information about a network.
They can generate reports showing utilization, errors and overall traffic
patterns on your network – reports that are very beneficial, as they show the
network growth over time. By watching
the growth, you can predict when problems may arise and take proactive steps
before they do.
2.4.3.1.3
Protocol Analyzers
Protocol
analyzers can do the job of network monitors, and much more. A protocol
analyser often proves to be an important tool when debugging problems on a
network. Also called network analyzers or sniffers,
protocol analyzers can be hardware only or a combination of hardware and/or
software. They collect information by examining all data going across the
network and decoding the information for display.
Some
problems that protocol analyzers can find are:
·
Bad network Cards
·
Bottlenecks
·
Configuration
errors in protocols
Protocol analyzers are excellent tools for
finding most problems on a network. They can look at the network packet by
packet and tell you exactly what is being transmitted. You may even use them to
debug network applications by looking at the ‘conversation’ going on.
Many administrators constantly keep a protocol
analyser working on their network. Most analyzers allow you to set threshold
levels for errors and other conditions – such as maximum number of collisions
per second or network utilization – and alert you when thresholds are reached.
Some popular protocol analyzers are Network
General’s sniffer, Hewlett-Packard’s Network Advisor, Novell’s LANalyzer and
Microsoft’s Network Monitor.
Many common protocol analyzers run on a normal
workstation computer. They use the workstation’s network hardware to access and
monitor the network. The correct choice of network card is important in the
computer that will be running the protocol analyzer software, as the network
card must be able to function in what is called promiscuous mode. Normally, the
MAC address on a network frame header is checked at the Data-Link layer. IF the
MAC address is found to be different from the computer reading it, it is
discarded. A network card in promiscuous mode passes all frames up to the
higher level processes, whether the frame was intended for it or not.
Some network cards will hide certain errors from
protocol analyzers because they can be given to upper-level processes. 3Com
network cards would commonly do this, as do most PCMCIA cards (used in laptop
computers).
Most Token Ring
networks cannot run in promiscuous mode. This is common with cards that have an
IBM chipset. Special Token Ring cards can be bough that do allow promiscuous
mode operation.
CHAPTER 3: Software Development
We studied the entire registration process and
realized that certain aspects of the process require a physical appearance of
the student:
1.
Verification of
Certificates
2.
Payment of fees
3.
Medical examination
and tests (Health Centre)
We designed a web chart that acts as a flowchart
outlining the process. The web chart also acts as flowchart for the entire
process, so it shows an outline of the registration process as well as a web
chart. Each process in the chart will be designed as a web page, to simplify
the entire thing.
The web chart is shown on the next page.
3.1 Hardware Examination
The process of optimising the network for the
program would involve equipment whose total cost runs into a few thousand
dollars. This was obviously a problem for us. What happened was that we
contacted Network General, a company that specialises into optimisation of
computer networks, and told them what we planned to do. They examined our
network diagrams and gave us five possible problems we could anticipate and
case studies of their clients who had encountered similar problems. With this
information, we could propose proactive solutions to the problems anticipated.
The five problems are outlined below.
3.1.1 Problem 1: New Client/Server Application Deployment
The actual deployment of our program may lead to
a problem in itself. No matter how well managed an existing client/server
system is new problems inevitably crop up when a new application is put on the
network. The roll-out of new client/server applications often causes problems
like sluggish performance, poor response time and even downtime. When new applications
are deployed in existing networks, they can affect the performance and
reliability of other applications on the network, e.g. email and Internet
services, in ways that are difficult to predict, understand, isolate and solve.
Problems can range from graceful degradation, to intermittent failure, to
disaster. Often higher levels of client/server protocols and long transaction
sequences must be understood to isolate faults. The costs – both the initial
problem solving and the additional maintenance required – are often not
anticipated in the original planning.
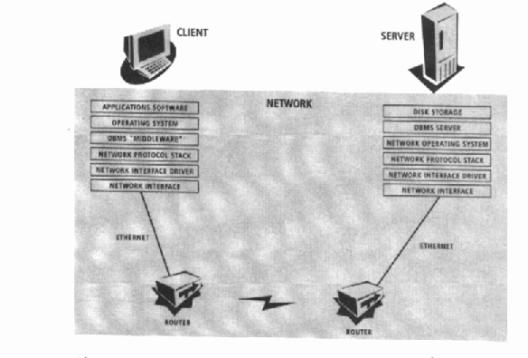
Figure 3.1: Client/Server Architecture
Some specific steps that can be taken in the
process of deploying the program:
Ø
Remember that the
performance and reliability of client/server applications are directly
dependent upon the performance and reliability of the network that carries
their communication, not the other way around.
Ø
To minimize
problems and optimise application performance, run the new application on a
limited test bed before you begin deployment.
Ø
To monitor
application performance and analyse any problems related to response time in
the test bed network, use distributed protocol analysis and troubleshooting
tools with visibility into all seven layers of the OSI model.
Ø
Identify and
resolve bottlenecks before deployment by evaluating the performance and
capacity of the production network to assess the network’s ability to support
the new application.
Ø
After you optimise
the new application’s performance, and tune the network, plan a staged
application roll-out to the entire enterprise.
Ø
Implement advanced
full-time proactive monitoring tools with high-level protocol decoders and
expert analysis upfront to help detect problems during testing phases, before
the network is affected.
Ø
Maintain
seven-layer network visibility. If the application is deployed and problems
exist, the better the visibility, the faster you can find a solution and
achieve the benefits of the new system.
Ø
Develop a written
deployment plan, then follow the plan using the right tools and training.
Correct application of these principles will
result in fewer problems and a smoother transition.
3.1.1.1 Case
Study
The benefits of proactive testing were understood
at a major insurance company in the USA; management wanted 300 Netware clients
in Accounting to have direct access to Human Resources information in an Oracle
database on a UNIX server.
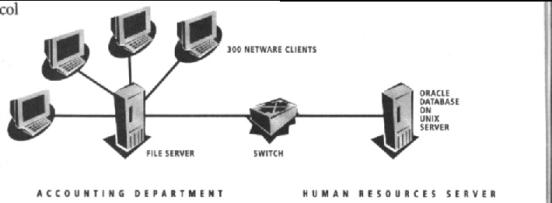
Figure 3.2: Case-Study
– Clients need to have access to Human Resources Server
One option was to upgrade the
NetWare clients with the necessary TCP/IP stack and Oracle TCP Protocol Adapter
software – costly and time consuming. The alternative was a less expensive
$1,500 Multi-Protocol Interchange (MPI) software upgrade to the NetWare server.
MPI software provides a gateway service that allows Oracle clients and servers
to communicate using different protocols.
Before approaching the latter, the IT manager wanted
assurance that this solution would not cripple the response time of important
and repetitive transactions caused by delays added by MPI software. Using the
Distributed Sniffer System (a product of Network General), the server upgrade
solution theory was tested. At the time, the longest transaction involved 200
packets, with a total response time of 2-3 seconds. Testing showed that users
were dissatisfied and less productive when response time approached six
seconds.
The Database Module measured the added latency of the MPI
software on the server to be acceptable: only five milliseconds/packet, or a
one-second addition in response time. The benefits of this proactive approach
were:
1.
Three hundred
tedious desktop software upgrades were avoided.
2.
A cost-saving
solution was deployed, satisfying management and users alike.
3.
The right decision
was made based on hard data,, not on conjecture and guesswork.
3.1.1.2 Application to this project
Before this program is deployed on
the entire network, we have to ensure that it is run for a particular period on
a test bed. We would run the network on a small section of the network, perhaps
Faculty of Sciences building, where it could be tested and any potential
problems could be discovered and possible solutions developed before the
program is employed network-wide. Also, the steps taken in the case study above
could also be employed, especially the use of the distributed Sniffer system,
which will not only help to solve this problem, but will also help further
proactive troubleshooting of the network.
3.1.2 Problem
2: Migrating to new technologies
Many
organisations have started using high-speed and switched network technologies
to improve network performance. Surprised at the unexpected problems, delays
and inefficiencies they quickly learn that adopting new technologies, while
essential can be time consuming and risky.
To reduce deployment time and lower risks, we
need a thorough understanding of the network and the new technologies – top to
bottom, end-to-end information. By combining RMON and other standards based
tools with distributed data collection and expert analysis consoles, we can get
a detailed understanding of traffic flow patterns, network utilization and
protocol turn-around times.
Since we plan to upgrade to switches, we need
solid information – not guesswork. Some steps we can take to get the
information we need are:
Ø
As we plan our
migration strategy, we should learn as much as we can about the network.
Ø
Employ device
analysis tools such as RouterPMTM and SwitchPMTM to
baseline the network to document trends and utilisation patterns, understand
where the critical segments, users, and applications are, as well as the impact
of downtime or poor performance, identify the segments that are candidates for
upgrade. Additionally, trending functionality helps you project when you will
need the capacity.
Ø
Use distributed protocol
analysis and troubleshooting tools with visibility into all seven layers of the
OSI model to gather information an application performance, top network
conservations, server bottlenecks, and more.
Ø
Based upon the
information obtained about the network, determine which elements of the
network; determine which elements of the network to upgrade to improve response
time for particular users.
Ø
Pinpoint
inefficiencies such as excessive retransmissions, time-out, unexpected network
hogs, and poor frame sizing so you can make more informed decisions about to
higher bandwidth network technologies or tuning your network.
Ø
Remember that what
works on a small scale in isolated network segment can bring the whole
enterprise down when deployed in quantity on the production network.
Ø
Use connectivity
and performance tools such as NETSYS products to create a modelling
environment. Then you can simulate using ‘what-if’ scenarios, allowing you to
effectively plan and implement upgrades, new technologies or routing changes.
Ø
Use network
performance test tools such as Chariot to test new technologies and devices and
to verify performance and capacity before buying and deploying new equipment.
Also, stress test new devices to certify reliability.
Ø
Design in fault and
performance management tools that match the needs of the new technologies; e.g.
purchasing FDDI and ISDN protocol analysers if installing FDDI backbones and
ISDN in remote branch offices.
3.1.2.1 Application to our project
In case the network is upgraded to
meet the demands of the high bandwidth needed by the program, we would probably
add switches to replace the hubs, which would increase the number of collision
domains, and therefore, the speed of the network. Addition of switches would
require training for the staff to learn how to configure them, and also, it
should be ensured that the addition of the switches would not add any new
problems to the network. We can use Network Monitor, software that comes free
with Microsoft Windows NT® , a network management tool,
that helps you to see what is happening on your network, to help find any
problems that occur due to the addition of the switches.
3.1.3 Problem
3: Poor Network Performance
Isolating
and solving poor network response time is one of a network manager’s biggest
frustrations. If poor network response time becomes chronic, the network
manager is put under stress, searching for bandwidth, bottlenecks or router
problems.
The complexity of today’s network is a factor. A
typical network transaction involves multiple vendors, technologies, sites and
potential points of failure. Poor network response time can be caused by a
variety of problems including inadequate bandwidth, network errors, server
bottlenecks, misconfigured routers, PC configuration errors, and inefficient
applications software.
Or the problem may be the result of the complex
end-to-end interaction of all these components. This problem, which is becoming
more common as the enterprise moves to client/server architectures, requires a
significant amount of time and energy, as well as various levels of technical
knowledge to isolate and resolve. Often, the problem is only resolved through a
combination of tedious hand-decoding of long transactions trace files, expert
knowledge, and time on the phone with several vendors.
Ø
Obtain total
visibility of the network. If you can’t see the cause of the problems, you
can’t solve the problems. Put into operation network fault and performance
management tools and systems that extend visibility beyond the LAN and into
applications, systems and databases. Partner with a network vendor that offers
proven experience and technology to help maximize network visibility.
Ø
Clearly define the
problem. A statement such as “the network is slow” describes a symptom, not the
root problem. You must narrow the problem down to a statement such as “the file
server does not respond fast enough to user requests because it does not have
the processing power”, so you can then decide if an increase in bandwidth or a
shift to micro segmentation will improve performance. Definitive, measurable
statements will help you find and fix the problem.
Ø
Employ expert-based
analysis systems. They speed resolution and can be upgraded over time, letting
you take advantage of the growing base of troubleshooting experience of the
other industry professionals.
Ø
Design into the
network powerful distributed monitoring systems as part of a full-time
management strategy. The data necessary to detect the source of slowly
degrading performance can be captured over time and solutions planned long
before users complain.
Ø
Consider building a
partnership relationship with a reliable provider of networking services. A
full-service partner can provide valuable expertise to planning to
troubleshooting.
3.1.3.1 Case
Study – Improving Network Performance
A major international insurer maintains its
leadership position by organising its global resources into a single enterprise
working toward common goals. The backbone of the enterprise is the extensive
LAN and WAN network connecting offices around the globe.
In
less than three months following the installation of the Distributed Sniffer
System, the company improved network response time by identifying where delays
took place and making necessary corrections.
In
one instance, desktop access to critical information on a VAX server was
improved by using the Distributed Sniffer System. By determining the time a
packet took to cross a switch, the distributed solution provided the key
information leading to the discovery of a bottleneck.
In
another instance, the Distributed Sniffer System successfully indicated that a
problem with a switch was causing a delay. The network administrator was able
to fix the problem locally and send a trace of the delay to a switch
manufacturer who used the information to correct the problem for users with
similar configurations. This proactive measure saved the insurer a tremendous
amount of time in troubleshooting other locations with related performance
problems.
The
benefits of this proactive approach were:
Ø
The root causes of
network performance problems were more easily and quickly identified and solved
using expert analysis.
Ø
Instead of dealing
with vendor finger-pointing, the insurance company was able to promptly
identify which vendor’s products were the cause of poor performance.
Ø
In many cases,
network performance problems were solved before users ever complained about
poor response time.
Ø
The insurance
company has increased overall productivity, as well as its ability to compete
in the marketplace, by proactively maintaining high network performance.
3.1.3.2 Application to our project
The OAU computer network has a very serious
problem concerning performance. The network is extremely slow especially when
using Internet services from the proxy server. Investigation revealed that the
Faculty of Science building network is operating at a speed of 2 Mbps, and the
link to computer building is also 2 Mbps. The rest of the school is also
operating at a similar speed. Before anything else, the network will need to be
upgraded to a speed of at least 10 Mbps.
3.1.4 Problem 4 – Not Enough Staff
Networks
grow in size and complexity, but the resources to manage them usually don’t
keep pace. Budgets are stretched. Existing staff must be leveraged as
effectively as possible.
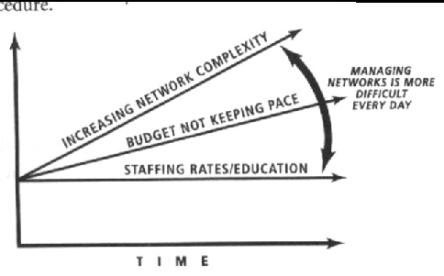
Figure 3.3 : The
widening gap between network complexity and network management resources
One
way to increase the effectiveness of your network management resources is to
improve the quality of your service.
Some
specific steps are:
Ø
Make proactive
network management your standard operating procedure. The best fault and
performance detection and correction tools must be designed into the network
and operated full time, rather than on a crisis basis.
Ø
Use expert systems,
which leverage the experience of others.
Ø
Integrate network
analysis tools to stretch your management resources.
Ø
Ask industry
vendors to work together more closely to solve problems and communicate
solutions to users.
Ø
Deploy advanced
tools with distributed data gathering devices and expert-based centralised
analysis consoles to help you monitor your entire network with fewer people,
solve problems faster and make better decisions for the future.
Ø
Utilize tools that
allow you to automate tasks, such as data gathering and report generation, as
much as possible.
Ø
Take advantage of
products that provide exception reports and high-level summaries. This
information can help you prioritise problems focus resources on the most
critical needs.
3.1.4.1 Case
Study – Maximizing Existing Resources
A
large government contractor had a network consisting of 50 Ethernet segments
with an FDDI backbone. The contractor’s three locations used WAN connections to
share a mission-critical project management application. Then a serious problem
developed: data was being lost over the WAN connections.
Four
trouble-shooters spent two weeks trying to diagnose the cause, with no results.
At night, they extensively tested network interface cards, routers and the WAN
connection. Finally, it seemed that a router was dropping packets, but the
cause could not be determined. After installing the Distributed Sniffer System,
the trouble-shooters used the expert analysis capabilities to zero in on the
problem – it was the application software itself. The acknowledgement time
pre-programmed in the software were insufficient for use over a WAN connection.
The solution was to dedicate a 10Mbps link for the critical application.
To
further maximise network performance, the contractor could implement a rules-based
analysis tool, such as RouterPM, to perform round-the-clock monitoring and
expert analysis of all router interfaces. Automatic analysis of data and
display of a prioritised list of potential problems allow a network manager to
take corrective action without having to wait until a failure or critical user
problem manifests itself. Additionally, partnering with a reliable provider of
networking services can give you the advantage of proven expertise in meeting
planning, design, implementation and management requirements.
The
benefits of using centralized problem-solving system were:
Ø
The Distributed
Sniffer System finds the causes of problems in minutes, not days, saving
critical time for the entire network management organization.
Ø
The distributed
fault and performance management solution realized cost saving in its very
first assignment. The Distributed Sniffer System was able to locate, in a
matter of minutes, a problem that stymied four people for a total of 120 hours
(Four people at $25/hour is $12,000, which greatly exceeds the investment in
the Distributed Sniffer System)
Ø
From a personnel
utilization standpoint, those four people could have been working on other
projects such as proactively optimising network performance to avoid problems
in the future.
3.1.4.2 Application to our project
The OAU computer network does not
appear to have the problem of staffing, but as the network grows, the staff
will also need to grow. Also, the staff should be given adequate training, do
as to keep up with the latest technology and also to make friends with other
Information Technology experts and form an expert system.
3.1.5 Problem 5 – Network Downtime
When
your network or part of it is unavailable, what does it cost? Today the
performance of the network is closely tied to the performance of the
organisation as a whole. If the program ever gets used, it would be disastrous
if the network failed at any time as NO WORK CAN DONE!!
Given
the complexity and nature of the technology, as well as human factors, some
network downtime is virtually unavoidable. However, networks can be designed to
recover more quickly from failures. Here are some specific steps you take to
reduce network downtime:
Ø
Identify all
mission critical network segments first. Determine what network segments,
routers, servers or other devices are absolutely essential to the daily
operations and health of the organisation.
Ø
Provide redundant
or backup systems that can be brought online quickly or even automatically
during failures.
Ø
Consider upgrading
to full-time network fault and performance systems. Rather than be reactive to
critical failures, it actually costs the organisation less money to be using a
proactive, full-time network communications management solution.
Ø
Use advanced tools
that help you quickly locate problems and determine their exact causes by
providing visibility into every layer of network traffic.
Ø
Measure and track
downtime with automated tools to help proactively identify problems and
document availability.
Ø
Stress test the network
after making off-hours equipment or configuration (e.g. router table) changes
did not adversely affect network connectivity, performance or reliability.
Ø
Use integrated
expert systems to provide the analysis to determine the root causes (not just
the symptoms) of problems and recommend solutions. Expert Systems can detect
problems at an overall lower cost than the low productivity from network
downtime.
3.1.5.1 Case
Study – Reducing Downtime
An
international airline relied on a network of 60 remote-token ring LANs with
Cisco and IBM source route bridges connected via high-speed internetwork links.
The network was used to process over 300,000 flights annually and provide
mission critical services for over 2,000 end users.
Users
of a critical application that ensured proper staffing of revenue-generating
routes began to have access problems. Without it, staffing for flights had to
be coordinated manually at a very high cost. There was also increased risk that
critical revenue-generating flights would go unstaffed and be unable to depart.
The
application resided on a remote file server, which generated TCP/IP traffic
across internetwork links to token ring segments. Isolating the problem in this
complex path was elusive. First it was assumed that it was Net BIOS related
because many of the company’s applications were built on Net BIOS and had a
history of excess bandwidth consumption problems in the network configuration.
The
Distributed Sniffer System was able to isolate the problem to a particular hardware
component on the internetwork link that was causing Cyclic Redundancy Check
(CRC) errors on large sized frames. Once the problem was identified, access to
the essential application was quickly restored.
The
benefits to this major airline were:
Ø
The cause of the
problem was pinpointed immediately, avoiding guesswork and speculation.
Ø
Network downtime
was eliminated in a mission critical revenue-generating application, allowing
the company to continue to be competitive and productive.
3.1.5.2
Application to our
project
The OAU computer network has no fault tolerance built into
it whatsoever, the network has been crippled several times, due to simple
faults. There should be alternate paths from the computer building that forms
loops on the network, so as to give a simple form of fault tolerance.
CHAPTER 4: Software Analysis
This chapter
discusses the project’s phases as experienced during the course of its
execution. It also seeks to compare the final output with the intended project
while not leaving out the reasons for such alterations.
As it is done
with any software development process, the following stages were encountered in
this project. They are Problem Definition, Program Design, Coding, Debugging,
Testing and Validation, Documentation, Maintenance, Extension and Redesign
experiences.
4.1 Problem
definition
As earlier
explained in the background, the problem of unnecessary multiple data, the
rigours of moving from location to location and the obvious inaccuracy in data
storage and retrieval prompted the actualisation of the project. With the
knowledge that a software-based system would reduce the bottlenecks, a proposal
was presented and work began on approval.
4.2 Program
Design
The need for
consultation could not have been eliminated in a project that has the potential
of changing the face of operations in the whole academic community. The
Registrar, Director of Academic Affairs, Information Technology and
Communication Unit’s point-man, and
Professor Kunle Kehinde (the project supervisor) threw light on various dark
spots of the project.
The webchart, describing the flow of the
entire work, was constructed and the hardware aspect was also taken into
consideration.
4.3 Coding and
Debugging
Armed with the
required skills in HTML and the Java flavour
(along with some other aids such as VBScript, image preparation tools and
materials from the various consultations), the coding began in stages and was
halted at the point where the database link gave problems. The problems were:
Ø
Improperly
installed Microsoft Access
Ø
Database link
problems
Ø
Irregular power
supply
The installation problem was tackled by re-installing the
software. The database link problems (which took majority of the problem-time) were faced with assistance
with downloaded codes on the Internet and consultations. There was no control
over the power supply but time management and a desperate lookout for power
supply helped the successful completion of the project.
Debugging commenced as soon as the project was completed and
errors were corrected with the major aim of the project in mind.
4.4 Testing and
validation
Sequel
to the major task of coding and debugging, the software had to be subjected to testing and validation to ensure the
durability and efficiency of the procedure. A series of database samples were
assumed and used for the testing. The major task of testing had to do with the
following:
- Ensuring
proper assessing of pages when links are clicked
- Ascertaining
that the VB Script and scripting codes carry out the
defined tasks by simulating results
- Editing
text to avoid embarrassing grammatical errors
The task of validating the software involved
testing raw data for processing in
the procedure.
4.5
Documentation
The beauty of any software design is
enhanced by the continuity of the project, i.e. the possibility of someone
other than the original author taking up the project and taking it to another
level of proficiency. The documentation of this project is considered necessary
since it is obviously an open-ended project.
The appendix
includes the source code and the statements within the code that can make
continuity possible.
4.6
Maintenance, Extension and Redesign
The maintenance
of the project is basically a post-implementation job and lies with the Network
Administrator and the major users of the software. The possibility of extending
and redesigning for a similar task would be made possible by the documentation
and the ease of use of the software.
Apart
from the usual steps or phases involved in the software design, another factor
of importance is the envisaged set of problems. They are:
- Possible
staff lay-off due to less demand for manpower
- Loss of
direct interaction between staff and students
- The
unavailability of an electronic
fund transfer system in the University
- The need
for any student to get physically to the Health Center for registration
and tests as may be suggested in the registration pack
- The
obvious necessity of verification of results due to standalone procedures
being operated by both the University and the West African Examination
Council.
CHAPTER 5: Conclusion and Recommendation
Having
weighed all possible sides of the project, it was discovered that it would
eventually be more advantageous to implement the software-based student
registration procedure.
The
following recommendations are thus put forth:
- That the
project should be implemented, maintained and monitored by the University
through its dynamic academic and institute staff membership
- That a
second phase of upgrading and constant redesign be put into perspective
even from now
- That the
members of staff that would be involved with either storage, retrieval or
processing of any information on the registration module be trained in the
art of computing
- That a
hardware upgrade for the intranet be considered. For instance, the
following locations need to be connected to the OAU Intranet for effective
actualisation of the project’s capabilities:
Ø
The Health Centre
complex
Ø
Division of Student
Affairs
Ø
All Halls of
residence
Ø
Faculty of
Administration
Ø
Faculty of Law
Ø
Faculty of Social
Sciences
Ø
Faculty of Pharmacy
Ø
Faculty of
Education
Ø
Faculty of Arts
Ø
Faculty of
Environmental design and Management
It would also be wise to
dedicate a particular Network
Administration Setup to the monitoring of the procedure. There is room for
expansion for the project to be upgraded to include:
Ø
Student
registration for non-freshers
Ø
Continuous
assessment result gathering and processing
Ø
Lecture notes for
students to download
Ø
Assignment upload
and grading facilities
Ø
A cyber-library
Ø
Secure Electronic
Fund Transfer
Ø
A networked
environment in relation to the Joint Admission Matriculation Board (JAMB) and
the West
African Examination Council (WAEC) for easier and more secure student
information processing
Ø
eHealth Facilities
for electronically driven health management systems via the school’s intranet.
Back to Top
REFERENCES
1.
Yesufu T.K. (2001), Lecture Notes on “EEE 510: Microcomputer Hardware
and Software Techniques”
2.
Ayara A.A. (2001) A seminar on “Internet Technologies and the Future of Nigeria”
delivered during the Electronic Week
2001 of the EEESS (Electronic and Electrical Students’ Society)
3.
A Handbook of “Proactive
Solutions to the Five Most Critical Networking Problems, A Network Visibility
Guide” compiled by the Staff of Network
General Inc. for the specific purpose of this project
4.
Nash, Jason (1999), Networking Essentials MCSE Study Guide
5.
Niemeyer, Patrick and Knudsen, Jonathan (2000), Learning Java
6.
Walsh, A.E. (1999), Java for dummies (3rd edition)
7.
Lemay, Laura and Cadenhead, Rogers (1999), SAMS Teach Yourself Java 2 in 21 days
8.
Buyens, Jim (1999), Running Microsoft FrontPage 2000
Back to Top
Appendix A – Source Code
Java Listing
GNUMakeFile
AnalogClock.class
CustomParser.class
JavaClock.class
JavaQuote.class
ParamParser.class
TextQuote.class
TextScript.class
HTML Code
Default.htm
<HTML>
<script
language="JavaScript">
<!--
// Number of visits variable :
var visits = 0;
var user = " " ;
3
// Standard cookie functions:
function extractCookieValue (val) {
if
((endOfCookie = document.cookie.indexOf(";", val)) == -1) {
endOfCookie
= document.cookie.length;
}
return
unescape(document.cookie.substring(val,endOfCookie));
}
function ReadCookie(cookiename) {
var
numOfCookies = document.cookie.length;
var
nameOfCookie = cookiename + "=";
var
cookieLen = nameOfCookie.length;
var
x = 0;
while
(x <= numOfCookies) {
var
y = (x + cookieLen);
if
(document.cookie.substring(x, y) == nameOfCookie)
return
(extractCookieValue(y));
x
= document.cookie.indexOf(" ", x) + 1;
if
(x == 0)
break;
}
return
(null);
}
function createCookie(name, value,
expiredays)
{
var
todayDate = new Date( ) ;
todayDate.setDate(todayDate.getDate(
) + expiredays);
document.cookie
= name +
"="
+
value
+
";
expires=" +
todayDate.toGMTString(
) +
";"
}
function showHits( ) {
//First we'll check if the user has visited
this page before by examining
//the _visitSite cookie:
userCookie =
ReadCookie("_visitSite");
userid = ReadCookie("username") ;
if (userCookie == null)
visits
= 1; //This is the first visit
else
visits
= parseInt(userCookie) + 1;
//
Create or update existing cookie:
createCookie("_visitSite",
visits, 30);
document.write("<div
align=center><font face=Verdana size=1 color=navy><b><font color=brown>Obafemi
Awolowo University</font></b>, Ile-Ife, Nigeria, welcomes you to
your visit number <b><font color=red>" +
visits
+
"</font></b>
in this site</font></div>");
}
//-->
</script>
<HEAD>
<META NAME="GENERATOR"
Content="Microsoft FrontPage 4.0">
<META
HTTP-EQUIV="Content-Type" content="text/html;
charset=iso-8859-1">
<TITLE>Student Registration
Procedure: A project by 'Gbenga Sesan and Bunmi Sowande</TITLE>
<bgsound src="music/02.mp3"
loop=infinite>
</HEAD>
<BODY>
<!--
document.cookie
= "username" +
"="
+
useid
+
";
expires=" +
todayDate.toGMTString(
) +
";"
-->
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<td bgcolor="#fdadad"
width="40%">
<table><tr><td>
<img valign=bottom align=left
src="oau0.jpg" alt="The Afrika theatre" border=0 height=50
width=50>
</td><td align=center>
<font size=1 face=Verdana
color=blue><b>Visit the <br><a
href="http://www.oauife.edu.ng">OBAFEMI AWOLOWO UNIVERSITY
website!</a></font>
</td></tr></table>
</td>
<td bgcolor="fcccfd">
<applet codebase="classes"
code="JavaQuote.class" width="400"
height="55">
<param name="bgcolor" value="fcccfd">
<param name="delay" value="1000">
<param name="space" value="20">
<param name="bwidth" value="10">
<param name="bheight" value="10">
<param name="random" value="true">
<param name="link"
value="http://java.sun.com/events/jibe/index.html">
<param name="fontname" value="TimesRoman">
<param name="fontsize" value="10">
<param name="number" value="3">
<param name="quote0" value="Obafemi Awolowo University is
a citadel of excellence with its tentacle of influence reaching into many
spheres of the Nigerian society.|- 'Gbenga Sesan.|000000|fcccfd|7">
<param name="quote1" value="This Java applet can be used
to display important information at intervals.|- Bunmi
Sowande|000000|fcccfd|7">
<param name="quote2" value="The project title is SOFTWARE
BASED STUDENT REGISTRATION PROCEDURE using Java and HTML and hosted on the
University Intranet.|- Prof. L. O. Kehinde|000000|fcccfd|7">
</applet>
</td>
<td bgcolor=fcfaad>
<applet codebase="clock
applet/classes" code="JavaClock.class" width="50"
height="50">
<param
name="delay" value="100">
<param
name="link"
value="http://java.sun.com/">
<param
name="border"
value="1">
<param
name="nradius" value="80">
<param
name="cfont"
value="TimesRoman|BOLD|8">
<param
name="bgcolor" value="fcfaad">
<param
name="shcolor" value="ff0000">
<param
name="mhcolor" value="00ff00">
<param
name="hhcolor" value="0000ff">
<param
name="ccolor"
value="dddddd">
<param
name="ncolor"
value="000000">
</applet>
</td>
</table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr bgcolor="#ccffed">
<td>
<script>
showHits( );
</script></td>
</tr></table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr>
<td width="20%"
bgcolor="fcccfd" valign=top>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr align=center valign=top><div
align=center valign=top>
<font size=1 face=Verdana><b>
<a
href="general.htm">General Information</a><p>
<a href="more.htm">More
Information</a><p>
<a href="form.htm">Start
Registration</a><p>
<a href="health.htm">Health
Services</a><p>
<a href="gallery/gallery.htm">OAU
in Pictures</a></b></font>
</div></tr>
</table>
</td>
<td width="80%" valign=top>
<div align=center><img
src="motion grd.jpg" width=300 alt="Motion ground: Adjacent to
the Senate building"> <img
src="motion grd2.jpg" width=300 alt="The
quadrangle"></div>
<div align=center><font size=2
color=navy>Please follow the links to the left to gain access to
some necessary information to guide you through this registration
procedure. You may choose to read the <b><a href="general.htm">General
Information</a></b> page
before proceeding to other pages. The forms
have been arranged such that the registration procedure is sequential and
thorough;
please follow the links.</font><hr>
<font face=Verdana size=1
color=brown><marquee><b>© 'Gbenga
Sesan and Bunmi Sowande 2001.</b></marquee>All
correspondence to <a
href="mailto:gbengasesan@yahoo.com">webmaster@gbengasesan.freeservers.com</a>
and <a
href="mailto:bsowande@beta.linkserve.com">webmaster@members.xoom.com/mrboso</a></font>
</div>
</td>
</table>
</table>
</BODY>
</HTML>
Exit.htm
<HTML>
<script
language="JavaScript">
<!--
// Number of visits variable :
var visits = 0;
var user = " " ;
3
// Standard cookie functions:
function extractCookieValue (val) {
if
((endOfCookie = document.cookie.indexOf(";", val)) == -1) {
endOfCookie
= document.cookie.length;
}
return
unescape(document.cookie.substring(val,endOfCookie));
}
function ReadCookie(cookiename) {
var
numOfCookies = document.cookie.length;
var
nameOfCookie = cookiename + "=";
var
cookieLen = nameOfCookie.length;
var
x = 0;
while
(x <= numOfCookies) {
var
y = (x + cookieLen);
if
(document.cookie.substring(x, y) == nameOfCookie)
return
(extractCookieValue(y));
x
= document.cookie.indexOf(" ", x) + 1;
if
(x == 0)
break;
}
return
(null);
}
function createCookie(name, value,
expiredays)
{
var
todayDate = new Date( ) ;
todayDate.setDate(todayDate.getDate(
) + expiredays);
document.cookie
= name +
"="
+
value
+
";
expires=" +
todayDate.toGMTString(
) +
";"
}
function showHits( ) {
//First we'll check if the user has visited
this page before by examining
//the _visitSite cookie:
userCookie =
ReadCookie("_visitSite");
userid = ReadCookie("username") ;
if (userCookie == null)
visits
= 1; //This is the first visit
else
visits
= parseInt(userCookie) + 1;
//
Create or update existing cookie:
createCookie("_visitSite",
visits, 30);
document.write("<div
align=center><font face=Verdana size=1 color=navy><b><font
color=brown>Obafemi Awolowo University</font></b>, Ile-Ife,
Nigeria, welcomes you to your visit number <b><font
color=red>" +
visits
+
"</font></b>
in this site</font></div>");
}
//-->
</script>
<HEAD>
<META NAME="GENERATOR"
Content="Microsoft FrontPage 4.0">
<META
HTTP-EQUIV="Content-Type" content="text/html;
charset=iso-8859-1">
<TITLE>Student Registration
Procedure: A project by 'Gbenga Sesan and Bunmi Sowande</TITLE>
<bgsound src="music/02.mp3"
loop=infinite>
</HEAD>
<BODY>
<!--
document.cookie
= "username" +
"="
+
useid
+
";
expires=" +
todayDate.toGMTString(
) +
";"
-->
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<td bgcolor="#fdadad"
width="40%">
<table><tr><td>
<img valign=bottom align=left
src="oau0.jpg" alt="The Afrika theatre" border=0 height=50
width=50>
</td><td align=center>
<font size=1 face=Verdana
color=blue><b>Visit the <br><a href="http://www.oauife.edu.ng">OBAFEMI
AWOLOWO UNIVERSITY website!</a></font>
</td></tr></table>
</td>
<td bgcolor="fcccfd">
<applet codebase="classes"
code="JavaQuote.class" width="400"
height="55">
<param name="bgcolor" value="fcccfd">
<param name="delay" value="1000">
<param name="space" value="20">
<param name="bwidth" value="10">
<param name="bheight" value="10">
<param name="random" value="true">
<param name="link"
value="http://java.sun.com/events/jibe/index.html">
<param name="fontname" value="TimesRoman">
<param name="fontsize" value="10">
<param name="number" value="3">
<param name="quote0" value="Obafemi Awolowo University is
a citadel of excellence with its tentacle of influence reaching into many
spheres of the Nigerian society.|- 'Gbenga Sesan.|000000|fcccfd|7">
<param name="quote1" value="This Java applet can be used
to display important information at intervals.|- Bunmi
Sowande|000000|fcccfd|7">
<param name="quote2" value="The project title is SOFTWARE
BASED STUDENT REGISTRATION PROCEDURE using Java and HTML and hosted on the
University Intranet.|- Prof. L. O. Kehinde|000000|fcccfd|7">
</applet>
</td>
<td bgcolor=fcfaad>
<applet codebase="clock
applet/classes" code="JavaClock.class" width="50"
height="50">
<param
name="delay"
value="100">
<param
name="link"
value="http://java.sun.com/">
<param
name="border"
value="1">
<param
name="nradius" value="80">
<param
name="cfont"
value="TimesRoman|BOLD|8">
<param
name="bgcolor" value="fcfaad">
<param
name="shcolor" value="ff0000">
<param
name="mhcolor" value="00ff00">
<param
name="hhcolor" value="0000ff">
<param
name="ccolor"
value="dddddd">
<param
name="ncolor"
value="000000">
</applet>
</td>
</table>
<table cellspacing=3 cellpadding=3 border=0
width="100%">
<tr bgcolor="#ccffed">
<td>
<script>
showHits( );
</script></td>
</tr></table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr>
<td width="20%"
bgcolor="fcccfd" valign=top>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr align=center valign=top><div
align=center valign=top>
<font size=1 face=Verdana><b>
<a
href="general.htm">General Information</a><p>
<a href="more.htm">More
Information</a><p>
<a href="health.htm">Health
Services</a><p>
<a href="gallery/gallery.htm">OAU
in Pictures</a></b></font>
</div></tr>
</table>
</td>
<td width="80%"
background=black>
<hr>
<font face=Verdana size=2
color=navy><div align=center>
This project is in fulfilment of the award
of <b>BSc</b> in Electronic and Electrical Engineering, Obafemi
Awolowo University, Ile-Ife, Nigeria.<p>
The project, supervised by
<b><i><a href="mailto:lkehinde@oauife.edu.ng">Prof
L. O. Kehinde</a></b></i>, was designed by <b><a
href="http://gbengasesan.netfirms.com">'Gbenga Sesan</a> and
<a href="http://www.members.xoom.com/mrboso">Bunmi
Sowande</a></b></div>
</font>
<hr>
<font face=Verdana size=1
color=brown><marquee><b>© 'Gbenga
Sesan and Bunmi Sowande 2001.</b></marquee>All
correspondence to <a
href="mailto:gbengasesan@yahoo.com">webmaster@gbengasesan.freeservers.com</a>
and <a
href="mailto:bsowande@beta.linkserve.com">webmaster@members.xoom.com/mrboso</a></font>
</div>
</td>
</table>
</table>
</BODY>
</HTML>
Form.htm
<HTML>
<script
language="JavaScript">
<!--
// Number of visits variable :
var visits = 0;
var user = " " ;
// Standard cookie functions:
function extractCookieValue (val) {
if
((endOfCookie = document.cookie.indexOf(";", val)) == -1) {
endOfCookie
= document.cookie.length;
}
return
unescape(document.cookie.substring(val,endOfCookie));
}
function ReadCookie(cookiename) {
var
numOfCookies = document.cookie.length;
var
nameOfCookie = cookiename + "=";
var
cookieLen = nameOfCookie.length;
var
x = 0;
while
(x <= numOfCookies) {
var
y = (x + cookieLen);
if
(document.cookie.substring(x, y) == nameOfCookie)
return
(extractCookieValue(y));
x
= document.cookie.indexOf(" ", x) + 1;
if
(x == 0)
break;
}
return
(null);
}
function createCookie(name, value,
expiredays)
{
var
todayDate = new Date( ) ;
todayDate.setDate(todayDate.getDate(
) + expiredays);
document.cookie
= name +
"="
+
value
+
";
expires=" +
todayDate.toGMTString(
) +
";"
}
function showHits( ) {
//First we'll check if the user has visited
this page before by examining
//the _visitSite cookie:
userCookie =
ReadCookie("_visitSite");
userid = ReadCookie("username") ;
if (userCookie == null)
visits
= 1; //This is the first visit
else
visits
= parseInt(userCookie) + 1;
//
Create or update existing cookie:
createCookie("_visitSite",
visits, 30);
document.write("<div
align=center><font face=Verdana size=1 color=navy><b><font
color=brown>Obafemi Awolowo University</font></b>, Ile-Ife,
Nigeria, welcomes you to your visit number <b><font
color=red>" +
visits
+
"</font></b>
in this site</font></div>");
}
//-->
</script>
<HEAD>
<META NAME="GENERATOR"
Content="Microsoft FrontPage 4.0">
<META
HTTP-EQUIV="Content-Type" content="text/html;
charset=iso-8859-1">
<TITLE>Student Registration
Procedure: Basic Student Bio-data Form</TITLE>
<bgsound src="shackles.mp3"
loop=infinite>
</HEAD>
<BODY>
<!--
document.cookie
= "username" +
"="
+
useid
+
";
expires=" +
todayDate.toGMTString(
) +
";"
-->
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<td bgcolor="#fdadad"
width="40%">
<table><tr><td>
<img valign=bottom align=left
src="oau0.jpg" alt="The Afrika theatre" border=0 height=50
width=50>
</td><td align=center>
<font size=1 face=Verdana
color=blue><b>Visit the <br><a
href="http://www.oauife.edu.ng">OBAFEMI AWOLOWO UNIVERSITY
website!</a></font>
</b>
</td></tr></table>
</td>
<td bgcolor="fcccfd">
<applet codebase="classes"
code="JavaQuote.class" width="400"
height="55">
<param name="bgcolor" value="fcccfd">
<param name="delay" value="1000">
<param name="space" value="20">
<param name="bwidth" value="10">
<param name="bheight" value="10">
<param name="random" value="true">
<param name="link"
value="http://java.sun.com/events/jibe/index.html">
<param name="fontname" value="TimesRoman">
<param name="fontsize" value="10">
<param name="number" value="3">
<param name="quote0" value="Obafemi Awolowo University is
a citadel of excellence with its tentacle of influence reaching into many
spheres of the Nigerian society.|- 'Gbenga Sesan.|000000|fcccfd|7">
<param name="quote1" value="This Java applet can be used
to display important information at intervals.|- Bunmi
Sowande|000000|fcccfd|7">
<param name="quote2" value="The project title is SOFTWARE
BASED STUDENT REGISTRATION PROCEDURE using Java and HTML and hosted on the
University Intranet.|- Prof. L. O. Kehinde|000000|fcccfd|7">
</applet>
</td>
<td bgcolor=fcfaad>
<applet codebase="clock
applet/classes" code="JavaClock.class" width="50"
height="50">
<param
name="delay"
value="100">
<param
name="link"
value="http://java.sun.com/">
<param
name="border"
value="1">
<param
name="nradius" value="80">
<param
name="cfont"
value="TimesRoman|BOLD|8">
<param
name="bgcolor" value="fcfaad">
<param
name="shcolor" value="ff0000">
<param
name="mhcolor" value="00ff00">
<param
name="hhcolor" value="0000ff">
<param
name="ccolor"
value="dddddd">
<param
name="ncolor"
value="000000">
</applet>
</td>
</table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr bgcolor="#ccffed">
<td>
<script>
showHits( );
</script></td>
</tr></table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr>
<td width="20%"
bgcolor="fcccfd" valign=top>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr><div align=center>
<font size=1 face=Verdana><b>
<a
href="general.htm">General Information</a><p>
<a href="health.htm">Health
Services</a><p>
<a href="default.htm">BACK
TO HOME</a><p></b></font>
</div></tr>
</table>
</td>
<td width="80%"
valign=absmiddle>
<table cellspacing=0 cellpadding=0
border=0 width="100%" height="1793">
<tr>
<td width="20%"
height="110"><img src="oaulogo.jpg" alt="oaulogo"
width=80></td>
<td width="80%"
height="110">
<p align="center"><b><font
color="brown" size="6">OBAFEMI AWOLOWO
UNIVERSITY,<br> ILE-IFE,
NIGERIA.</font></b></td>
</tr>
<form method=post
action="response.htm">
<tr>
<td colspan=2 align=center width="100%"
height="179">
<hr><p><font
color="#800000">Please <i> enter</i> your
<b>names </b>in the spaces indicated below and ensure that
you enter all other details in the form
accurately. All confidential
details </font></p><hr>
<p><b><font color="#FF00FF"
face="Arial Black">GENERAL STUDENT
INFORMATION</font></b></p>
<p><b><font face=Verdana
color=#000080 size=2>Surname</font><font face=Verdana color=navy
size=2>:</font></b><font face=Verdana color=navy
size=2><input type=text name=surname size=15
maxlength=25> </font><b><font face=Verdana
color=#000080 size=2>Other
names</font><font face=Verdana
color=navy size=2>:</font></b><font face=Verdana color=navy
size=2><input type=text name=othernames size=22 maxlength=35>
</font></p>
</td>
</tr>
<tr><td colspan=2
height="1504">
<font face=Verdana color=navy size=2>
<p>
<p><b>Date of Birth:</b>
<select name=birthday size=1>
<option selected>1
<option>2
<option>3
<option>4
<option>5
<option>6
<option>7
<option>8
<option>9
<option>10
<option>11
<option>12
<option>13
<option>14
<option>15
<option>16
<option>17
<option>18
<option>19
<option>20
<option>21
<option>22
<option>23
<option>24
<option>25
<option>26
<option selected>27
<option>28
<option>29
<option>30
<option>31
</select>
<select size=1 name=birthmonth>
<option>Jan
<option>Feb<option>Mar<option>Apr<option>May<option>Jun<option
selected>Jul<option>Aug<option>Sep<option>Oct<option>Nov<option>Dec
</select>
<input type=text name=birthyear
size=6>
<p><b>Place of
Birth:</b> <input type=text name=birthplace1 size=36>
<p>
<b>Sex:</b><select size=1
name=sex>
<option selected>Male
<option>Female</select>
<b>Marital
Status:</b><select size=1 name=mstatus><option
selected>Single<option>Married<option>Divorced<option>Widowed</select>
<b>State:</b><select
size=1 name=state><option>Abia<option>Adamawa<option>Akwa
Ibom<option>Anambra<option>Bauchi<option>Bayelsa<option>Benue<option>Borno<option>Cross
River<option>Delta<option>Ebonyi<option>Edo<option>Ekiti<option>Enugu<option>Gombe<option>Imo<option>Jigawa<option>Kaduna<option>Kano<option>Katsina<option>Kebbi<option>Kogi<option>Kwara<option>Lagos<option>Nassarawa<option>Niger<option>Ogun<option
selected>Ondo<option>Osun<option>Oyo<option>Plateau<option>Rivers<option>Sokoto<option>Taraba<option>Yobe<option>Zamfara<option>Abuja</select>
<p>
<b>Local
Government:</b><input type=text name=locagov size=15
maxlength=30> <b>Nationality:</b><input type=text
name=nationality size=15 maxlength=35>
<p>
<b><u>ADDRESSES</u>:</b><br>
<div align=center>
<b>Student Contact
Address:</b><br>
<textarea cols=40 rows=6
name=scaddy></textarea><p>
<b>Student Permanent Home
Address:</b><br>
<textarea cols=40 rows=6
name=sphaddy></textarea><p>
<b>Parent/Guardian Name and
Address:</b><br>
<textarea cols=40 rows=6
name=sgnaddy></textarea><p>
<b>Next-Of-Kin Name and
Address:</b><br>
<textarea cols=40 rows=6
name=nknaddy></textarea><p>
<b>Sponsor's Name and
Address:</b><br>
<textarea cols=40 rows=6
name=snaddy></textarea>
</div>
<hr>
</font>
<p
align="center"><b><font color="#FF00FF"
face="Arial Black" size="2">ACADEMIC
INFORMATION</font></b></p>
<font face=Verdana color=navy size=2>
<b>Faculty:</b><input
type=text name=faculty size=15
maxlength=25> <b>Department:</b><input type=text
name=department size=20 maxlength=35><p>
<b>Course of
Study:</b><input type=text name=cstudy size=20
maxlength=35> <b>Degree:</b><input
type=text name=degree size=10 maxlength=15><p>
<b>Current
Session:</b><input type=text name=csession
size=9> <b>Semester:</b><select name=csemester
size=1><option
selected>Harmattan<option>Rain</select> <b>Part:</b><select
name=cpart size=1><option selected>1<option>2<option>3<option>4<option>5<option>6<option>7<option>8<option>9</select><p>
<b>Mode of
entry:</b><br><input type=radio name=mentry
value="ume">UME<p>
<input type=radio name=mentry
value="direct">Direct<p>
<input type=radio name=mentry
value="transfer">Transfer<p>
<b>If transfer, name of previous
University:</b> <input type=text name=university size=20
maxlength=40>
</font>
<p align="center">
<font face=Verdana color=navy size=2>
<b>Special Electives of
Choice:</b></p>
<font face=Verdana color=navy size=2>
<p align="center">
<textarea cols=40 rows=6 name=selectives></textarea>
</font></font>
<p align="center">
<div
align="center"><table bgcolor="white"
cellpadding="3" cellspacing=3>
<tr>
<td align=middle colspan=2
bgcolor="navy"><font color="yellow">Please input
your name, UME Registration number and examination score. Please note that name
must be as reflected on UME Registration slip.</font>
</td>
</tr>
<tr>
<th align="right"><font
color=navy>Name</font></th>
<td align="left">
<p><input type="text" size="40"
name="umename" maxlength="80"></p>
</td>
</tr>
<tr>
<th align="right"><font
color=navy>Registration Number</font></th>
<td align="left">
<p><input type="text" size="20"
name="umeregno" maxlength="20"></p>
</td>
</tr>
<tr>
<th align="right"><font
color=navy>UME Score</font></th>
<td align="left">
<p><input
type="text" size="4" name="umescore"
maxlength="8"></p>
</td>
</tr>
</table>
<hr>
<p align="center">
<b><font face="Arial
Black" size="2" color="#FF00FF">HEALTH
INFORMATION</font></b>
<p align="center">
<b><font face="verdana"
size="2" color=navy>Please indicate any Medical problems you think
we need to know (in few words):</font><br>
<textarea cols=40 rows=6
name=health></textarea>
</font>
<hr>
<font face=Verdana color=navy size=2>
<p>
<b>Please input your receipt number
(from fee payment) here:<input type="password"
name="pay" length=10 maxlength=20><p><hr>
<div align=center><input
type=submit name=action></div><hr>
</form>
</td></tr>
</table>
</td>
</table>
</table>
</BODY>
</HTML>
Gallery.htm
<html>
<head>
<bgsound src="music/.mp3"
loop="11">
<title>'Gbenga Sesan and Bunmi
Sowande 2001</title>
<bgsound src="7.mp3">
</head>
<body bgcolor="0000">
<div align="center">
<center>
<table border="0" width="500"
height="300">
<td width="430" height="295"><applet
code="DemoWebpage.class" width=589 height=340>
<param name="totalimages"
value="27">
<param name="imagename"
value="p">
<param name="sleeptime"
value="1000">
</applet>
</table>
</center>
<hr>
<marquee><font face=Verdana size=3
color=skyblue><b>Scenes from Obafemi awolowo University, Ile-Ife,
Nigeria. Just like yesterday...This page is dedicated to our most honourable
supervisor, Professor L. O. Kehine, we will miss you.
Thanks...</b></font></marquee>
<hr><br>
<div align=center>
<a
href="javascript:history.back(1)"><font size=1>| BACK
|</font></a>
</div>
</div>
</body>
</html>
General.htm
<HTML>
<script
language="JavaScript">
<!--
// Number of visits variable :
var visits = 0;
var user = " " ;
// Standard cookie functions:
function extractCookieValue (val) {
if
((endOfCookie = document.cookie.indexOf(";", val)) == -1) {
endOfCookie
= document.cookie.length;
}
return
unescape(document.cookie.substring(val,endOfCookie));
}
function ReadCookie(cookiename) {
var
numOfCookies = document.cookie.length;
var
nameOfCookie = cookiename + "=";
var
cookieLen = nameOfCookie.length;
var
x = 0;
while
(x <= numOfCookies) {
var
y = (x + cookieLen);
if
(document.cookie.substring(x, y) == nameOfCookie)
return
(extractCookieValue(y));
x
= document.cookie.indexOf(" ", x) + 1;
if
(x == 0)
break;
}
return
(null);
}
function createCookie(name, value,
expiredays)
{
var
todayDate = new Date( ) ;
todayDate.setDate(todayDate.getDate(
) + expiredays);
document.cookie
= name +
"="
+
value
+
";
expires=" +
todayDate.toGMTString(
) +
";"
}
function showHits( ) {
//First we'll check if the user has visited
this page before by examining
//the _visitSite cookie:
userCookie =
ReadCookie("_visitSite");
userid = ReadCookie("username") ;
if (userCookie == null)
visits
= 1; //This is the first visit
else
visits
= parseInt(userCookie) + 1;
//
Create or update existing cookie:
createCookie("_visitSite",
visits, 30);
document.write("<div
align=center><font face=Verdana size=1 color=navy><b><font
color=brown>Obafemi Awolowo University</font></b>, Ile-Ife,
Nigeria, welcomes you to your visit number <b><font
color=red>" +
visits
+
"</font></b>
in this site</font></div>");
}
//-->
</script>
<HEAD>
<META NAME="GENERATOR"
Content="Microsoft FrontPage 4.0">
<META
HTTP-EQUIV="Content-Type" content="text/html;
charset=iso-8859-1">
<TITLE>Student Registration
Procedure: A project by 'Gbenga Sesan and Bunmi Sowande</TITLE>
<bgsound src="heart.mp3"
loop=infinite>
</HEAD>
<BODY>
<!--
document.cookie
= "username" +
"="
+
useid
+
";
expires=" +
todayDate.toGMTString(
) +
";"
-->
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<td bgcolor="#fdadad"
width="40%">
<table><tr><td>
<img valign=bottom align=left
src="oau0.jpg" alt="The Afrika theatre" border=0 height=50
width=50>
</td><td align=center>
<font size=1 face=Verdana
color=blue><b>Visit the <br><a
href="http://www.oauife.edu.ng">OBAFEMI AWOLOWO UNIVERSITY
website!</a></font>
</td></tr></table>
</td>
<td bgcolor="fcccfd">
<applet codebase="classes"
code="JavaQuote.class" width="400"
height="55">
<param name="bgcolor" value="fcccfd">
<param name="delay" value="1000">
<param name="space" value="20">
<param name="bwidth" value="10">
<param name="bheight" value="10">
<param name="random" value="true">
<param name="link"
value="http://java.sun.com/events/jibe/index.html">
<param name="fontname" value="TimesRoman">
<param name="fontsize" value="10">
<param name="number" value="3">
<param name="quote0" value="Obafemi Awolowo University is
a citadel of excellence with its tentacle of influence reaching into many
spheres of the Nigerian society.|- 'Gbenga Sesan.|000000|fcccfd|7">
<param name="quote1" value="This Java applet can be used
to display important information at intervals.|- Bunmi
Sowande|000000|fcccfd|7">
<param name="quote2" value="The project title is SOFTWARE
BASED STUDENT REGISTRATION PROCEDURE using Java and HTML and hosted on the
University Intranet.|- Prof. L. O. Kehinde|000000|fcccfd|7">
</applet>
</td>
<td bgcolor=fcfaad>
<applet codebase="clock
applet/classes" code="JavaClock.class" width="50"
height="50">
<param
name="delay"
value="100">
<param
name="link"
value="http://java.sun.com/">
<param
name="border"
value="1">
<param
name="nradius" value="80">
<param
name="cfont"
value="TimesRoman|BOLD|8">
<param
name="bgcolor" value="fcfaad">
<param
name="shcolor" value="ff0000">
<param
name="mhcolor" value="00ff00">
<param
name="hhcolor" value="0000ff">
<param
name="ccolor"
value="dddddd">
<param
name="ncolor"
value="000000">
</applet>
</td>
</table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr bgcolor="#ccffed">
<td>
<script>
showHits( );
</script></td>
</tr></table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr>
<td width="20%"
bgcolor="fcccfd" valign=top>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr><div align=center>
<font size=1
face=Verdana><b><hr color="fcccfd">
<a href="default.htm">BACK
HOME</a><p>
<a href="health.htm">Health
Services</a><p>
<a href="women.htm">For
Women Students</a><p>
<a href="form.htm">Start
Registration</a><p>
<a href="more.htm">More
Information</a><p>
</b></font>
</div></tr>
</table>
</td>
<td width="80%" valign=top>
<font size=2>
<h1 align=center><font
color=navy>GENERAL INFORMATION</font></h1>
I am pleased to welcome you to this
University and hope you will have a successful career here. I give below some
important items of information for your close attention:<p>
<h3><u><font
color=green>Entrance Medical Examination</font></u></h3>
All freshmen are advised to read the
instruction on the <a href="health.htm">Entrance Medical Examination</a>
page. It is important that all <font colo=blue>freshmen</font>
complete the Medical Forms accordingly. Students will not be allowed entry into
Halls of Residence and/or lectures until their Medical reports are received by
the <b><i>Director of Medical and Health
Services</i></b>, Health Center, Obafemi Awolowo
University, Ile-Ife. In addition, they will
not enjoy University Medical facilities. It is important to note especially
that <i>Blood</i>, <i>Stool</i>
and <i>Urine</i> investigations
should be done at the University Health Centre.<p>
<h3><u><font
color=green>Dress and daily necessities</font></u></h3>
Students will not be required to wear
<b>uniforms</b> but will be expected to maintain a high standard of
neatness in their clothes and
surroundings. Students may, on
<i>academic grounds</i>, be required to wear undergraduate gowns
which are, at present, available on loan from the University.
For students who have secured accommodation
in the Halls of Residence, the following will be required for daily use:
<ol
type=a><b><li>Mattress (6" X
2<sup>1</sup>/<sub>2</sub>") to be provided by
students
<li>Toilet necessities e.g. soap etc.
<li>Towels
<li>Night wear or pajamas
<li>Sport wear - White shorts or
trousers</b></ol>
<h3><u><font color=green>Verification
of documents/Registration</font></u></h3>
The West African Examination Council (WAEC)
has confirmed that the <font
color=blue><b><i>Certificates</i></b></font>
of candidates who sit for examinations would be prepared quickly and made
available for collection. All freshmen are therefore required to bring with
them <b>original</b> documents supporting their qualifications.
Such documents will be carefully
scrutinized during the registration exercise and students who fail to
produce their original <u>certificates</u> accordingly will
<u><i>not</i></u> be registered.<br>
However, it is the responsibility of each
student to ensure the security of his/her original certificates.
<b>Receipts for fees paid should also be produced at the time of registration
for courses.</b>
<h3><u><font
color=green>Accommodation in the Halls of
Residence</font></u></h3>
Admission into the University does not mean
automatic admission into the Halls of Residence. Admission to a Hall of
Residence is by application to the <b>Dean of Student Affairs</b>.
Accommodation is automatic for first year
students and would be allocated on
completion of registration.<br>
While students are not obliged to live in
the Halls, those who elect to do so must conform with certain regulations, the
adherence to which will enable every student have a pleasant stay in residence.
Students who are unsuccessful in obtaining accommodation in a University Hall
of Residence shall make their own arrangements for lodging outside the Campus.
<b>Freshmen will be provided accommodation on priority basis</b>.
<h3><u><font
color=green>Code of Conduct for Students</font></u></h3>
Every student is expected to get himself/herself familiarised with the
<b>Code of Conduct</b> for students as
approved by <font color=red>Governing Council</font> with
effect from <i>25<sup>th</sup> November,
1990</i>.<b> In addition, students
should not belong to <font
color=navy>secret societies</font>.</b>
<h3><u><font
color=green><i>Change of Name</i> by Students of the University</font></u></h3>
It is very important to note that all
students shall graduate with names by which they are admitted into the
University and hat such names may only change consequent upon changes in
<b><i>marital status</i></b> (in case of female students).<p>
<hr color=white><b>Once again,
please accept my congratulations on your admission into <a
href="http://www.oauife.edu.ng">Obafemi Awolowo
University</a>. I hope you will have a pleasant time throughout the
period of your studentship in our University.</b><p>
Thank you.<p>
<div
align=right><b><i><font
color="#abadca">Principal Assistant Registrar
(Admissions)</font></i></b></div>
<hr>
<div align=center><font
face=Verdana size=1
color=brown><marquee>© 'Gbenga
Sesan and Bunmi Sowande 2001.</marquee></font></div>
<div align=center><font
face=Verdana size=1 color=brown>All co</font></font><font
face="Verdana" size="1"
color="brown">r</font><font size=2><font
face=Verdana size=1 color=brown>respondence to <a
href="mailto:gbengasesan@yahoo.com">webmaster@gbengasesan.freeservers.com</a>
and <a
href="mailto:bsowande@beta.linkserve.com">webmaster@members.xoom.com/mrboso</a></font></div>
</font>
</td>
</table>
</table>
</BODY>
</HTML>
Health.htm
<HTML>
<script
language="JavaScript">
<!--
// Number of visits variable :
var visits = 0;
var user = " " ;
// Standard cookie functions:
function extractCookieValue (val) {
if
((endOfCookie = document.cookie.indexOf(";", val)) == -1) {
endOfCookie
= document.cookie.length;
}
return
unescape(document.cookie.substring(val,endOfCookie));
}
function ReadCookie(cookiename) {
var
numOfCookies = document.cookie.length;
var
nameOfCookie = cookiename + "=";
var
cookieLen = nameOfCookie.length;
var
x = 0;
while
(x <= numOfCookies) {
var
y = (x + cookieLen);
if
(document.cookie.substring(x, y) == nameOfCookie)
return
(extractCookieValue(y));
x
= document.cookie.indexOf(" ", x) + 1;
if
(x == 0)
break;
}
return
(null);
}
function createCookie(name, value,
expiredays)
{
var
todayDate = new Date( ) ;
todayDate.setDate(todayDate.getDate(
) + expiredays);
document.cookie
= name +
"="
+
value
+
";
expires=" +
todayDate.toGMTString(
) +
";"
}
function showHits( ) {
//First we'll check if the user has visited
this page before by examining
//the _visitSite cookie:
userCookie =
ReadCookie("_visitSite");
userid = ReadCookie("username") ;
if (userCookie == null)
visits
= 1; //This is the first visit
else
visits
= parseInt(userCookie) + 1;
//
Create or update existing cookie:
createCookie("_visitSite",
visits, 30);
document.write("<div
align=center><font face=Verdana size=1 color=navy><b><font
color=brown>Obafemi Awolowo University</font></b>, Ile-Ife,
Nigeria, welcomes you to your visit number <b><font
color=red>" +
visits
+
"</font></b>
in this site</font></div>");
}
//-->
</script><HEAD>
<META NAME="GENERATOR"
Content="Microsoft FrontPage 4.0">
<META
HTTP-EQUIV="Content-Type" content="text/html;
charset=iso-8859-1">
<TITLE>Student Registration
Procedure: A project by 'Gbenga Sesan and Bunmi Sowande</TITLE>
</HEAD>
<BODY>
<!--
document.cookie
= "username" +
"="
+
useid
+
";
expires=" +
todayDate.toGMTString(
) +
";"
-->
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<td bgcolor="#fdadad"
width="40%">
<table><tr><td>
<img valign=bottom align=left
src="oau0.jpg" alt="The Afrika theatre" border=0 height=50
width=50>
</td><td align=center>
<font size=1 face=Verdana
color=blue><b>Visit the <br><a
href="http://www.oauife.edu.ng">OBAFEMI AWOLOWO UNIVERSITY
website!</a></b></font>
</td></tr></table>
</td>
<td bgcolor="fcccfd">
<applet codebase="classes"
code="JavaQuote.class" width="400"
height="55">
<param name="bgcolor" value="fcccfd">
<param name="delay" value="1000">
<param name="space" value="20">
<param name="bwidth" value="10">
<param name="bheight" value="10">
<param name="random" value="true">
<param name="link"
value="http://java.sun.com/events/jibe/index.html">
<param name="fontname" value="TimesRoman">
<param name="fontsize" value="10">
<param name="number" value="3">
<param name="quote0" value="Obafemi Awolowo University is
a citadel of excellence with its tentacle of influence reaching into many
spheres of the Nigerian society.|- 'Gbenga Sesan.|000000|fcccfd|7">
<param name="quote1" value="This Java applet can be used
to display important information at intervals.|- Bunmi
Sowande|000000|fcccfd|7">
<param name="quote2" value="The project title is SOFTWARE
BASED STUDENT REGISTRATION PROCEDURE using Java and HTML and hosted on the
University Intranet.|- Prof. L. O. Kehinde|000000|fcccfd|7">
</applet>
</td>
<td bgcolor=fcfaad>
<applet codebase="clock
applet/classes" code="JavaClock.class" width="50"
height="50">
<param
name="delay"
value="100">
<param
name="link"
value="http://java.sun.com/">
<param
name="border"
value="1">
<param
name="nradius" value="80">
<param
name="cfont"
value="TimesRoman|BOLD|8">
<param
name="bgcolor" value="fcfaad">
<param
name="shcolor" value="ff0000">
<param
name="mhcolor" value="00ff00">
<param
name="hhcolor" value="0000ff">
<param
name="ccolor"
value="dddddd">
<param
name="ncolor"
value="000000">
</applet>
</td>
</table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr bgcolor="#ccffed">
<td>
<script>
showHits( );
</script></td>
</tr></table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr>
<td width="20%"
bgcolor="fcccfd" valign=top>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr><div align=center>
<font size=1
face=Verdana><b><hr color="fcccfd">
<a href="default.htm">BACK
HOME</a><p>
<a
href="general.htm">General Information</a><p>
<a href="women.htm">For
Women Students</a><p>
<a href="form.htm">Start
Registration</a><p>
</b></font>
</div></tr>
</table>
</td>
<td width="80%" valign=top>
<font size=2>
<h1 align=center><font
color="navy">UNIVERSITY HEALTH SERVICES</font></h1>
<p align=left>1. All freshmen are
expected during the first week of resumption
to register at the <b>Health
Centre</b>. <b><i>Blood, Stool and Urine
</i></b>investigations
must be performed at the University Health
Centre.</p>
<p align=left>(a) The <b>Medical
Questionnaire <font color="#FF0000">(at the
health section of the <a
href="form.htm">Student Information
form</a>)</font></b>
should be carefully
filled<i><b> </b></i>before arrival at the Health
Centre.
Note that <b>it is a confidential
report and shall not be used against your
admission.</b></p>
<p align=left>(b) The Medical Form
should be carefully filled.</p>
<p align=left>(c) After
<b><i>Blood, Stool and Urine </i></b>investigation at
the Health Centre, the physical Examination
will be conducted by Medical Doctors
at the University Health Centre.</p>
<p align=left>(d) The cost of the 3
investigations listed in (c) above is
<b><strike>N</strike>300..00
(cash)</b>.</p>
<p align=left>(e) <font
color="#800000"><b>Condition for Matriculation.
</b></font>It
is an offence against University
Regulations for a student not to register at
the Health Centre. You will not be allowed
to matriculate unless you register at
the Health Centre.</p>
<p align=left>2. The Health Centre
offers a twenty-four-hours, round-the-clock
service. Doctors are in attendance between
<b>7:30am and 3:30pm </b>on week
days, <b>11:00am and 12:00</b>
noon on Saturdays, Sundays and Public Holidays to
attend to emergencies or continue special
treatment. At other times, a Nursing
Sister/Superintendent is on duty with other
Nurses and will summon a doctor as
the condition of the patient may
warrant.</p>
<p align=left>(a) Whenever possible,
a student desiring to consult a doctor
should attend during the doctor's normal
hors of duty.</p>
<p align=left>(b) In a medical
emergency, the student who is ill should arrange
to inform the Porter on duty in his or her
hall of residence. The Porter
on duty will report immediately to the
Nursing Sister or Superintendent on duty
at the Health Centre.</p>
<p align=left>(c) Students are
requested to bring their Health Centre Cards
whenever they report sick at the Health
Centre.</p>
<p align=left>(d) Difficulties or
complaints arising from services at the Health
Centre should be reported to the Director
of Medical and Health Services.</p>
<p align=left> </p>
<div
align=right><b><i><font
color="#abadca">Principal Assistant Registrar
(Admissions)</font></i></b></div>
<hr>
<div align=center><font
face=Verdana size=1 color=brown><marquee>© 'Gbenga
Sesan and Bunmi Sowande 2001.</marquee></font></div>
<div align=center><font
face=Verdana size=1 color=brown>All co</font></font><font
face="Verdana" size="1"
color="brown">r</font><font size=2><font
face=Verdana size=1 color=brown>respondence to <a
href="mailto:gbengasesan@yahoo.com">webmaster@gbengasesan.freeservers.com</a>
and <a
href="mailto:bsowande@beta.linkserve.com">webmaster@members.xoom.com/mrboso</a></font></div>
</font>
</td>
</table>
</table>
</body>
</html>
More.htm
<HTML>
<script
language="JavaScript">
<!--
// Number of visits variable :
var visits = 0;
var user = " " ;
// Standard cookie functions:
function extractCookieValue (val) {
if
((endOfCookie = document.cookie.indexOf(";", val)) == -1) {
endOfCookie
= document.cookie.length;
}
return
unescape(document.cookie.substring(val,endOfCookie));
}
function ReadCookie(cookiename) {
var
numOfCookies = document.cookie.length;
var
nameOfCookie = cookiename + "=";
var
cookieLen = nameOfCookie.length;
var
x = 0;
while
(x <= numOfCookies) {
var
y = (x + cookieLen);
if
(document.cookie.substring(x, y) == nameOfCookie)
return
(extractCookieValue(y));
x
= document.cookie.indexOf(" ", x) + 1;
if
(x == 0)
break;
}
return
(null);
}
function createCookie(name, value,
expiredays)
{
var
todayDate = new Date( ) ;
todayDate.setDate(todayDate.getDate(
) + expiredays);
document.cookie
= name +
"="
+
value
+
";
expires=" +
todayDate.toGMTString(
) +
";"
}
function showHits( ) {
//First we'll check if the user has visited
this page before by examining
//the _visitSite cookie:
userCookie =
ReadCookie("_visitSite");
userid = ReadCookie("username") ;
if (userCookie == null)
visits
= 1; //This is the first visit
else
visits
= parseInt(userCookie) + 1;
//
Create or update existing cookie:
createCookie("_visitSite",
visits, 30);
document.write("<div
align=center><font face=Verdana size=1 color=navy><b><font
color=brown>Obafemi Awolowo University</font></b>, Ile-Ife,
Nigeria, welcomes you to your visit number <b><font
color=red>" +
visits
+
"</font></b>
in this site</font></div>");
}
//-->
</script>
<HEAD>
<META NAME="GENERATOR"
Content="Microsoft FrontPage 4.0">
<META
HTTP-EQUIV="Content-Type" content="text/html;
charset=iso-8859-1">
<TITLE>Student Registration
Procedure: A project by 'Gbenga Sesan and Bunmi Sowande</TITLE>
<bgsound src="heart.mp3"
loop=infinite>
</HEAD>
<BODY>
<!--
document.cookie
= "username" +
"="
+
useid
+
";
expires=" +
todayDate.toGMTString(
) +
";"
-->
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<td bgcolor="#fdadad"
width="40%">
<table><tr><td>
<img valign=bottom align=left
src="oau0.jpg" alt="The Afrika theatre" border=0 height=50
width=50>
</td><td align=center>
<font size=1 face=Verdana
color=blue><b>Visit the <br><a
href="http://www.oauife.edu.ng">OBAFEMI AWOLOWO UNIVERSITY
website!</a></font>
</td></tr></table>
</td>
<td bgcolor="fcccfd">
<applet codebase="classes"
code="JavaQuote.class" width="400"
height="55">
<param name="bgcolor" value="fcccfd">
<param name="delay" value="1000">
<param name="space" value="20">
<param name="bwidth" value="10">
<param name="bheight" value="10">
<param name="random" value="true">
<param name="link"
value="http://java.sun.com/events/jibe/index.html">
<param name="fontname" value="TimesRoman">
<param name="fontsize" value="10">
<param name="number" value="3">
<param name="quote0" value="Obafemi Awolowo University is
a citadel of excellence with its tentacle of influence reaching into many
spheres of the Nigerian society.|- 'Gbenga Sesan.|000000|fcccfd|7">
<param name="quote1" value="This Java applet can be used
to display important information at intervals.|- Bunmi
Sowande|000000|fcccfd|7">
<param name="quote2" value="The project title is SOFTWARE
BASED STUDENT REGISTRATION PROCEDURE using Java and HTML and hosted on the
University Intranet.|- Prof. L. O. Kehinde|000000|fcccfd|7">
</applet>
</td>
<td bgcolor=fcfaad>
<applet codebase="clock
applet/classes" code="JavaClock.class" width="50"
height="50">
<param
name="delay"
value="100">
<param
name="link"
value="http://java.sun.com/">
<param
name="border"
value="1">
<param
name="nradius" value="80">
<param
name="cfont"
value="TimesRoman|BOLD|8">
<param
name="bgcolor" value="fcfaad">
<param
name="shcolor" value="ff0000">
<param
name="mhcolor" value="00ff00">
<param
name="hhcolor" value="0000ff">
<param
name="ccolor"
value="dddddd">
<param
name="ncolor"
value="000000">
</applet>
</td>
</table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr bgcolor="#ccffed">
<td>
<script>
showHits( );
</script></td>
</tr></table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr>
<td width="20%"
bgcolor="fcccfd" valign=top>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr><div align=center>
<font size=1
face=Verdana><b><hr color="fcccfd">
<a href="default.htm">BACK
HOME</a><p>
<a href="health.htm">Health
Services</a><p>
<a href="women.htm">For
Women Students</a><p>
<a href="form.htm">Start
Registration</a><p>
<a href="more.htm">More
Information</a><p>
</b></font>
</div></tr>
</table>
</td>
<td width="80%" valign=top>
<font size=2>
<h1 align=center><font
color="navy">MORE INFORMATION</font></h1>
<p align=left><b><span
style="text-transform: capitalize">A. Registration for
courses:</span></b></p>
<p align=left>(i) Freshmen will fill
the form on the <b><a href="form.htm">Student
Information Page</a>, </b>which
combines the:</p>
<p align=left><b>MIS
01(<i>Students Information form</i>), MIS 02 (<i>Course
Registration form</i>), Health Centre
Questionnaire,</b></p>
<p align=left><b>ISR 04
(<i>Course Registration Cards</i>), ISR 01 (<i>Basic
Student Bio-data
form)</i></b></p>
<p align=left>The contents of the
form would be retrieved by the appropriate
quarters from the University's central
database.</p>
<p align=left>(ii) The list of
courses to be registered for during each Semester
(or Session for Faculties not operating the
course unit system) will be made
available by the Head of Department, and
would be accessible online.</p>
<p align=left>(iii) The minimum
number of units are required for full-time
student is 15 units while the maximum is 24
units.</p>
<p align=left> </p>
<p align=left><b>B. Exemption
form special electives:</b></p>
<p align=left>(i) That graduates of
the University who had previously passed the
old <i>GNS</i> courses should
be exempted automatically from taking special
electives for purposes of fulfilling the
requirements for graduation.</p>
<p align=left>(ii) That in the case
of graduates from other recognized
Universities and candidates transferring
from other Universities/Higher
Institutions, the general studies courses
taken by such students in their old
Institutions should be evaluated and
processed for exemption by Senate where
appropriate.</p>
<p align=left> </p>
<p align=left><b>C. Change of
electives:</b></p>
<p align=left>Change of electives,
particularly restricted electives, should be
made only within the group of courses
approved for a particular semester.</p>
<p align=left> </p>
<p align=left><b>D.
Administration of Examination:</b></p>
<p align=left>(a) The person who
teaches a course will be charged with
invigilation during the examination for
that course.</p>
<p align=left>(b) Where courses are
large in terms of student enrolment and cut
across disciplines, the Faculties in which
the courses are based will be made
responsible for invigilation during the
examination for those courses.</p>
<p align=left>(c) The setting,
moderation and presentation of examination papers
to students in courses based in Departments
should be the responsibility
of individual Departments.</p>
<p align=left>(d) Efforts should be
made to ensure that examination results are
ready before registration for the following
Semester.</p>
<p align=left>(f) Competence in terms
of academic and administrative leadership
should be emphasized in assigning persons
the responsibility of Chief Examiners.</p>
<p align=left>(g) The Departmental
Examiners should meet and prepare provisional
results within 4 working days after the
submission of examination grades.</p>
<p align=left>(h) The provisional
results approved by the Faculty Board of
Examiners should be used for registration
purposes.</p>
<p align=left>(i) Henceforth, the
University should provide stationery for
examinations so as to assist Faculties in
processing examination results.</p>
<p align=left>(j) The examination
results of graduating students should be
processed for the approval of
Senate. any result that is treated
administratively for the purposes of
<b><i>NYSC</i></b> should be processed
later for the approval of Senate.
The results of non-graduating students
should be processed later of the approval
of the Committee of Deans.</p>
<p align=left><b>E. Code of
Conduct for the University community as approved by
Council with effect from 25th November,
1990</b></font>.</p>
<p align=left><font size=2>That
an academic staff shall not favour any student
by disclosing examination questions before
the scheduled time for such
examinations or by awarding unearned grades
or by acting in any other manner
inconsistent with his or her status as a
University Examiner.</p>
<p align=left><b>F. Examination
Malpractice</b></p>
<p align=left>(i) Cases of
examination malpractice should be submitted by the
Invigilators to the Dean of the Faculty
within 24 hours of the examination
period.</p>
<p align=left>(ii) The result of any
student involved in examination malpractice
should be withheld until the case is
disposed of.</p>
<p align=left>(iii) Faculty
Examination Malpractice Committee should consider
such cases and make appropriate recommendations
to the Vice-Chancellor within
two months.</p>
<p align=left><b>G. Withdrawal
from the University</b></p>
<p align=left>(i) That for Faculties
running the Course Unit System, a student
should be allowed an additional period of
50% of the duration of his programme
after which his studentship should be
deemed to have lapsed whether or not he
has a <b>C.G.P.A. of
1.00</b>. The decision took effect from the beginning
of 1996/97 academic session.</p>
<p align=left>(ii) That for the
Faculties of Clinical Sciences, Dentistry and
Pharmacy, a student should not be allowed
to repeat a year more than once.</p>
<p align=left>(iii) That the period,
i.e., the duration of programme, should
exclude approved periods of leave of
absence granted to the student.</p>
<p align=left>(iv) That students on
ground should be given additional 50% of the
remaining period to complete their
programmes.</p>
<p align=left>(v) That the existing
Regulation on probation should be retained.</p>
<p align=left>(vi) The names of students
asked to withdraw from the University
should be processed to Senate for approval
prompt.</p>
<p align=left><b>H. Intention
to graduate:</b></p>
<p align=left>Students, in their
final sessions, must indicate their
interest in concluding their academic
responsibilities by filling out
appropriate forms that would be made
available on demand.</p>
<p align=left><b>I. Tutorial
List</b></p>
<p align=left>A tutorial list of
students is always kept in other to monitor the
students taking a course and to prepare the
continuous assessment details from
time to time. Students should ensure that
their names are correctly indicated on
the list.</p>
<div
align=right><b><i><font
color="#abadca">Principal Assistant Registrar
(Admissions)</font></i></b></div>
<hr>
<div align=center><font
face=Verdana size=1
color=brown><marquee>© 'Gbenga
Sesan and Bunmi Sowande 2001.</marquee></font></div>
<div align=center><font
face=Verdana size=1 color=brown>All co</font></font><font
face="Verdana" size="1" color="brown">r</font><font
size=2><font face=Verdana size=1 color=brown>respondence to <a
href="mailto:gbengasesan@yahoo.com">webmaster@gbengasesan.freeservers.com</a>
and <a href="mailto:bsowande@beta.linkserve.com">webmaster@members.xoom.com/mrboso</a></font></div>
</font>
</td>
</table>
</table>
</BODY>
</HTML>
Origin.htm
<html>
<head>
<meta name="generator"
Content="Microsoft FrontPage 4.0">
<meta http-equiv="refresh"
content="8;URL=welcome.htm">
<title>Welcome to our Obafemi Awolowo
University, Ile-Ife</title>
<bgsound src="explore.wav">
</head>
<body bgcolor=black>
<table border=0
align=center><tr><td>
<hr size=90 color=black>
<hr size=40 color=black>
<img src="welcome.gif">
</td></tr></table>
</html>
Response.htm
<HTML>
<script language="JavaScript">
<!--
// Number of visits variable :
var visits = 0;
var user = " " ;
3
// Standard cookie functions:
function extractCookieValue (val) {
if
((endOfCookie = document.cookie.indexOf(";", val)) == -1) {
endOfCookie
= document.cookie.length;
}
return
unescape(document.cookie.substring(val,endOfCookie));
}
function ReadCookie(cookiename) {
var
numOfCookies = document.cookie.length;
var
nameOfCookie = cookiename + "=";
var
cookieLen = nameOfCookie.length;
var
x = 0;
while
(x <= numOfCookies) {
var y = (x + cookieLen);
if
(document.cookie.substring(x, y) == nameOfCookie)
return
(extractCookieValue(y));
x
= document.cookie.indexOf(" ", x) + 1;
if
(x == 0)
break;
}
return
(null);
}
function createCookie(name, value, expiredays)
{
var
todayDate = new Date( ) ;
todayDate.setDate(todayDate.getDate(
) + expiredays);
document.cookie
= name +
"="
+
value
+
";
expires=" +
todayDate.toGMTString(
) +
";"
}
function showHits( ) {
//First we'll check if the user has visited
this page before by examining
//the _visitSite cookie:
userCookie =
ReadCookie("_visitSite");
userid = ReadCookie("username") ;
if (userCookie == null)
visits
= 1; //This is the first visit
else
visits
= parseInt(userCookie) + 1;
//
Create or update existing cookie:
createCookie("_visitSite",
visits, 30);
document.write("<div
align=center><font face=Verdana size=1 color=navy><b><font
color=brown>Obafemi Awolowo University</font></b>, Ile-Ife,
Nigeria, welcomes you to your visit number <b><font
color=red>" +
visits
+
"</font></b>
in this site</font></div>");
}
//-->
</script>
<HEAD>
<META NAME="GENERATOR"
Content="Microsoft FrontPage 4.0">
<META
HTTP-EQUIV="Content-Type" content="text/html; charset=iso-8859-1">
<TITLE>Student Registration
Procedure: A project by 'Gbenga Sesan and Bunmi Sowande</TITLE>
</HEAD>
<BODY>
<!--
document.cookie
= "username" +
"="
+
useid
+
";
expires=" +
todayDate.toGMTString(
) +
";"
-->
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<td bgcolor="#fdadad"
width="40%">
<table><tr><td>
<img valign=bottom align=left
src="oau0.jpg" alt="The Afrika theatre" border=0 height=50
width=50>
</td><td align=center>
<font size=1 face=Verdana
color=blue><b>Visit the <br><a
href="http://www.oauife.edu.ng">OBAFEMI AWOLOWO UNIVERSITY
website!</a></font>
</td></tr></table>
</td>
<td bgcolor="fcccfd">
<applet codebase="classes"
code="JavaQuote.class" width="400"
height="55">
<param name="bgcolor" value="fcccfd">
<param name="delay" value="1000">
<param name="space" value="20">
<param name="bwidth" value="10">
<param name="bheight" value="10">
<param name="random" value="true">
<param name="link"
value="http://java.sun.com/events/jibe/index.html">
<param name="fontname" value="TimesRoman">
<param name="fontsize" value="10">
<param name="number" value="3">
<param name="quote0" value="Obafemi Awolowo University is
a citadel of excellence with its tentacle of influence reaching into many
spheres of the Nigerian society.|- 'Gbenga Sesan.|000000|fcccfd|7">
<param name="quote1" value="This Java applet can be used
to display important information at intervals.|- Bunmi
Sowande|000000|fcccfd|7">
<param name="quote2" value="The project title is SOFTWARE
BASED STUDENT REGISTRATION PROCEDURE using Java and HTML and hosted on the
University Intranet.|- Prof. L. O. Kehinde|000000|fcccfd|7">
</applet>
</td>
<td bgcolor=fcfaad>
<applet codebase="clock
applet/classes" code="JavaClock.class" width="50"
height="50">
<param
name="delay"
value="100">
<param
name="link"
value="http://java.sun.com/">
<param
name="border"
value="1">
<param
name="nradius" value="80">
<param
name="cfont"
value="TimesRoman|BOLD|8">
<param
name="bgcolor" value="fcfaad">
<param
name="shcolor" value="ff0000">
<param
name="mhcolor" value="00ff00">
<param
name="hhcolor" value="0000ff">
<param
name="ccolor"
value="dddddd">
<param
name="ncolor"
value="000000">
</applet>
</td>
</table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr bgcolor="#ccffed">
<td>
<script>
showHits( );
</script></td>
</tr></table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr>
<td width="20%"
bgcolor="fcccfd" valign=top>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr align=center valign=top><div
align=center valign=top>
<font size=1 face=Verdana><b>
<a
href="general.htm">General Information</a><p>
<a href="more.htm">More
Information</a><p>
<a href="health.htm">Health
Services</a><p>
<a
href="exit.htm">Exit</a><p>
<a
href="gallery/gallery.htm">OAU in
Pictures</a></b></font>
</div></tr>
</table>
</td>
<td width="80%">
<hr>
<font face=Verdana size=2 color=navy>
Thank you for taking time to fill the form
correctly. Your information has been entered into the Intranet database and
would be used for all necessary processes without bothering you with the stress
of filling out any forms.
<p>
<b><font color=brown>Your matricultaion
number is <font
color=navy>EEE/2001/001</font></font><br>
<b><font color=brown>Your
accommodation allocation is <font color=navy>Room 8, Block H, Angola
Hall</font></font><br>
<b><font color=brown>Your
appointment with the Health Centre is at <font color=navy>9:00am on
Tuesday, 27th September, 2002</font></font><br>
<b><font color=brown>Your
appointment for Certificate (SSCE, NECO, GCE) screening is at the Faculty
Office on <font color=navy>Wednesday, 28th September, 2002 at
10:30am</font></font><br>
<p>
Once again,
<b>congratulations</b> on your admission to this citadel of
learning.
</font>
<hr>
<font face=Verdana size=1
color=brown><marquee><b>© 'Gbenga
Sesan and Bunmi Sowande 2001.</b></marquee>All
correspondence to <a
href="mailto:gbengasesan@yahoo.com">webmaster@gbengasesan.freeservers.com</a>
and <a
href="mailto:bsowande@beta.linkserve.com">webmaster@members.xoom.com/mrboso</a></font>
</div>
</td>
</table>
</table>
</BODY>
</HTML>
Welcome.htm
<html>
<head>
<meta name="generator"
Content="Microsoft FrontPage 4.0">
<meta http-equiv="refresh"
content="15;URL='default.htm'">
<meta http-equiv="Page-Enter"
content="revealTrans(Duration=4.0,Transition=0)">
<meta http-equiv="Page-Exit"
content="revealTrans(Duration=4.0,Transition=blend)">
<title>Welcome to our Obafemi Awolowo
University, Ile-Ife</title>
<bgsound src="start.wav"
loop="3">
</head>
<body bgcolor="00FFFF">
<basefont face=Verdana>
<div align=center>
<font color=red
size=6>O b a f e m i
<font color=red
size=6>A w o l o w o
<font color=red
size=6>U n i v e r s i t y<p>
<font color="336600"
size=4><b>I l e - I f e, N i g e r i a.</b><p>
<table cellpadding=5 cellspacing=0
width="100%" border=0><tr><td align=center>
<img
src="oau0.jpg"></td><td align=center><img
src="oau1.jpg"></td></tr></table>
<p><div align=center><b><font
color=navy size=2>The most beautiful <font
color=brown>Campus</font> in Africa</b></div><p>
<marquee><font color=red
size=1><i><b>"For Learning and
Culture"</b></i></font></marquee></div>
</html>
Women.htm
<HTML>
<script language="JavaScript">
<!--
// Number of visits variable :
var visits = 0;
var user = " " ;
// Standard cookie functions:
function extractCookieValue (val) {
if
((endOfCookie = document.cookie.indexOf(";", val)) == -1) {
endOfCookie
= document.cookie.length;
}
return
unescape(document.cookie.substring(val,endOfCookie));
}
function ReadCookie(cookiename) {
var
numOfCookies = document.cookie.length;
var
nameOfCookie = cookiename + "=";
var
cookieLen = nameOfCookie.length;
var
x = 0;
while
(x <= numOfCookies) {
var
y = (x + cookieLen);
if
(document.cookie.substring(x, y) == nameOfCookie)
return
(extractCookieValue(y));
x
= document.cookie.indexOf(" ", x) + 1;
if
(x == 0)
break;
}
return
(null);
}
function createCookie(name, value, expiredays)
{
var
todayDate = new Date( ) ;
todayDate.setDate(todayDate.getDate(
) + expiredays);
document.cookie
= name +
"="
+
value
+
";
expires=" +
todayDate.toGMTString(
) +
";"
}
function showHits( ) {
//First we'll check if the user has visited
this page before by examining
//the _visitSite cookie:
userCookie =
ReadCookie("_visitSite");
userid = ReadCookie("username") ;
if (userCookie == null)
visits
= 1; //This is the first visit
else
visits
= parseInt(userCookie) + 1;
//
Create or update existing cookie:
createCookie("_visitSite",
visits, 30);
document.write("<div
align=center><font face=Verdana size=1 color=navy><b><font
color=brown>Obafemi Awolowo University</font></b>, Ile-Ife,
Nigeria, welcomes you to your visit number <b><font
color=red>" +
visits
+
"</font></b>
in this site</font></div>");
}
//-->
</script>
<HEAD>
<META NAME="GENERATOR"
Content="Microsoft FrontPage 4.0">
<META
HTTP-EQUIV="Content-Type" content="text/html; charset=iso-8859-1">
<TITLE>Information for Women
Students</TITLE>
<bgsound src="power.mp3"
loop=infinite>
</HEAD>
<BODY>
<!--
document.cookie
= "username" +
"="
+
useid
+
";
expires=" +
todayDate.toGMTString(
) +
";"
-->
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<td bgcolor="#fdadad"
width="40%">
<table><tr><td>
<img valign=bottom align=left
src="oau0.jpg" alt="The Afrika theatre" border=0 height=50
width=50>
</td><td align=center>
<font size=1 face=Verdana
color=blue><b>Visit the <br><a
href="http://www.oauife.edu.ng">OBAFEMI AWOLOWO UNIVERSITY
website!</a></font>
</td></tr></table>
</td>
<td bgcolor="fcccfd">
<applet codebase="classes"
code="JavaQuote.class" width="400"
height="55">
<param name="bgcolor" value="fcccfd">
<param name="delay" value="1000">
<param name="space" value="20">
<param name="bwidth" value="10">
<param name="bheight" value="10">
<param name="random" value="true">
<param name="link"
value="http://java.sun.com/events/jibe/index.html">
<param name="fontname" value="TimesRoman">
<param name="fontsize" value="10">
<param name="number" value="3">
<param name="quote0" value="Obafemi Awolowo University is
a citadel of excellence with its tentacle of influence reaching into many
spheres of the Nigerian society.|- 'Gbenga Sesan.|000000|fcccfd|7">
<param name="quote1" value="This Java applet can be used
to display important information at intervals.|- Bunmi
Sowande|000000|fcccfd|7">
<param name="quote2" value="The project title is SOFTWARE
BASED STUDENT REGISTRATION PROCEDURE using Java and HTML and hosted on the
University Intranet.|- Prof. L. O. Kehinde|000000|fcccfd|7">
</applet>
</td>
<td bgcolor=fcfaad>
<applet codebase="clock
applet/classes" code="JavaClock.class" width="50"
height="50">
<param
name="delay"
value="100">
<param
name="link"
value="http://java.sun.com/">
<param
name="border"
value="1">
<param
name="nradius" value="80">
<param
name="cfont"
value="TimesRoman|BOLD|8">
<param
name="bgcolor" value="fcfaad">
<param
name="shcolor" value="ff0000">
<param
name="mhcolor" value="00ff00">
<param
name="hhcolor" value="0000ff">
<param
name="ccolor"
value="dddddd">
<param
name="ncolor"
value="000000">
</applet>
</td>
</table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr bgcolor="#ccffed">
<td>
<script>
showHits( );
</script></td>
</tr></table>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr>
<td width="20%"
bgcolor="fcccfd" valign=top>
<table cellspacing=3 cellpadding=3
border=0 width="100%">
<tr><div align=center>
<font size=1
face=Verdana><b><hr color="fcccfd">
<a href="default.htm">BACK
HOME</a><p>
<a href="health.htm">Health
Services</a><p>
<a href="general.htm">Back
to General Information</a><p>
<a href="form.htm">Start
Registration</a><p>
</b></font>
</div></tr>
</table>
</td>
<td width="80%" valign=top>
<font size=2>
<h1 align=center><font
color=navy>INFORMATION FOR WOMEN STUDENTS</font></h1>
The <b>Advisory Committee on Student
Affairs</b> has approved the following conditions for treatment in the
University for <i>Women Undergraduates</i>:<p>
<ol><li>Ease of undergraduate
access to <i>obstetric facilities</i> cannot at this stage of
University development be guaranteed. Until
facilities improve and can be considered adequate, the University is
unable to accept liability of pregnant students. This
<a href="health.htm">University Health
Services</a> will undertake to advise and direct students generally as
may be necessary.
<li>A married student becoming
pregnant will report her condition early to the Mistress of the Hall and Chief
Medical Officer. The Chief Medical Officer will inform the Registrar of her
state indicating her expected date of delivery.
<li>The <b>husband</b> of
a pregnant student or the <i>potential father</i> of her expected
baby will produce to the Registrar a written undertaking accepting the
responsibility for the student's condition and any complications of it. He will
make necessary arrangements for her ante-natal care, surveillance and delivery.
<li>An undergraduate who delays in
reporting her <b>pregnancy</b> which is detected only because it
becomes obvious to non-medical observers will be ejected from her hall of
residence at seventy-two hours notice.
<li>The University will not be
responsible for the obstetric expenses of a pregnant student unless she is by
virtue of being the wife of a member of staff otherwise qualified.
<li>Pregnant undergraduates will be
allowed to remain in their Halls of Residence and take part as fully as they
may wish in al University activities until <b>six weeks</b> before
their expected date of delivery when they shall move out of the campus and will
be barred from all Lectures and Seminars until six weeks after delivery. During
this <b><i>three-month period</i></b>, they will not be
allowed to take any University examination.
<li>An expectant, unmarried student
who will not or cannot identify a potential father shall be sent down from the
University by the Registrar until six weeks after the
delivery of the baby.</ol>
</font>
<hr>
<div align=center>
<font face=Verdana size=1
color=brown><marquee>© 'Gbenga Sesan
and Bunmi Sowande
2001</marquee></font>
</div>
<div align=center>
<font face=Verdana size=1
color=brown>All correspondence to <a
href="mailto:gbengasesan@yahoo.com">webmaster@gbengasesan.freeservers.com</a>
and <a
href="mailto:bsowande@beta.linkserve.com">webmaster@members.xoom.com/mrboso</a></font>
</div>
</td>
</table>
</table>
</BODY>
</HTML>
Back to Top
Appendix B – Sample Screen Shots
Screen Shot 1: The Default Page
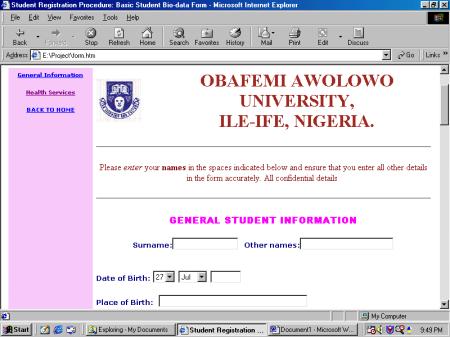
Screen Shot 2: The Form Page
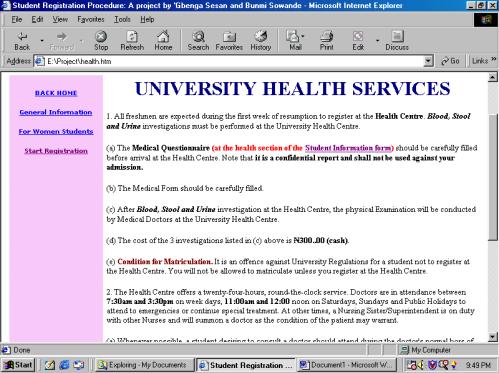
Screen Shot 3: Health Information Page
Screen Shot 4: Confirmation Page
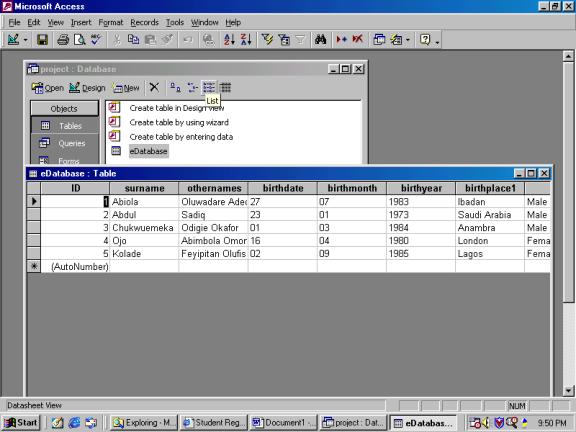
Screen Shot 5: Database Structure
